HP Neoware e90 Neoware Firewall User Manual - Page 11
Adding a New Filter, Defining Filter Rules, a Filter, Filter Name, Filter Action, Permit, Block
 |
View all HP Neoware e90 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 11 highlights
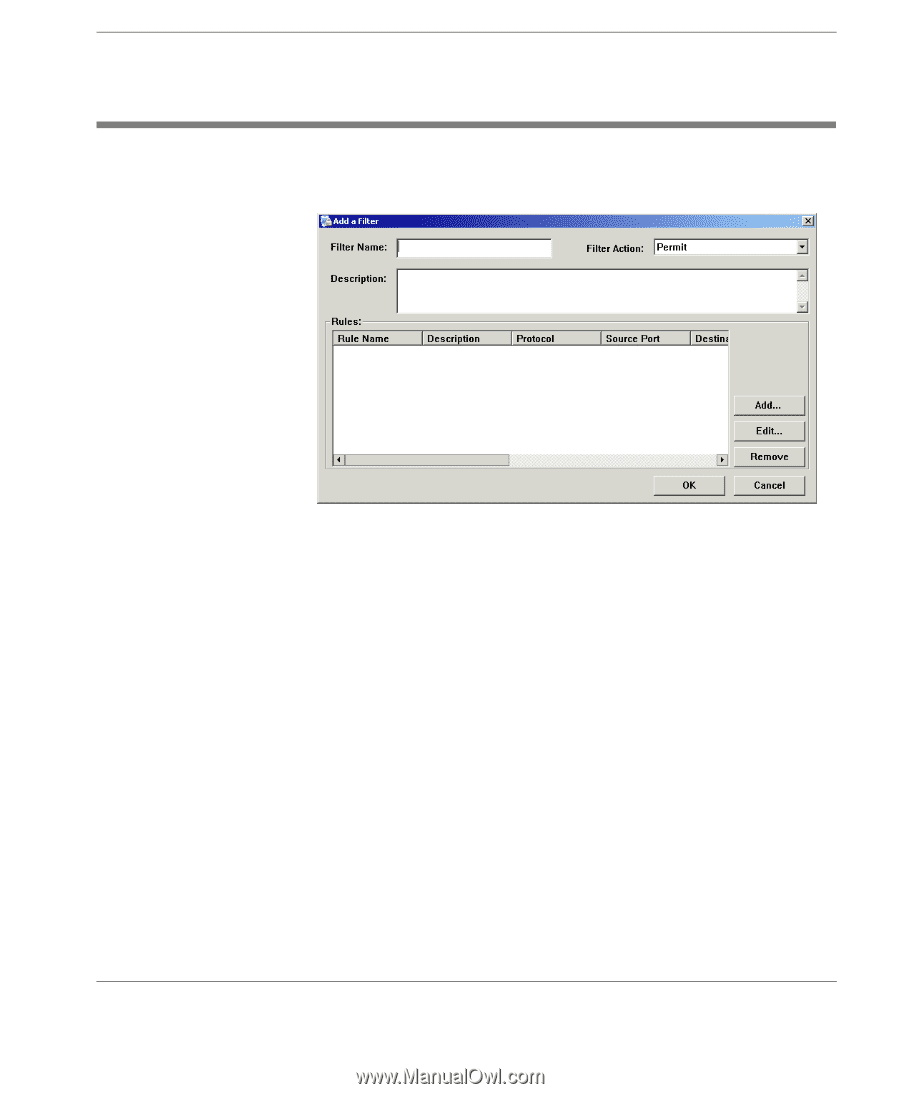
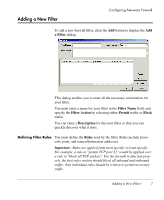
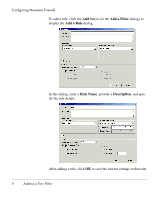
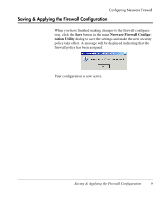
Adding a New Filter Configuring Neoware Firewall To add a new firewall filter, click the Add button to display the Add a Filter dialog. This dialog enables you to enter all the necessary information for your filter. You must enter a name for your filter in the Filter Name field, and specify the Filter Action by selecting either Permit traffic or Block traffic. You can enter a Description for this new filter so that you can quickly discover what it does. Defining Filter Rules You must define the Rules used by the filter. Rules include protocols, ports, and source/destination addresses. Important: Rules are applied from most specific to least specific. For example, a rule to "permit TCP port 21" would be applied over a rule to "block all TCP packets". For the firewall to function properly, the first rules written should block all inbound and outbound traffic, then individual rules should be written to permit necessary traffic. Adding a New Filter 7