Konica Minolta bizhub PRO 951 bizhub PRO 951 Security User Guide - Page 61
Analyzing Audit Log, Audit log information, Table of items saved in audit log - how to change time
 |
View all Konica Minolta bizhub PRO 951 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 61 highlights
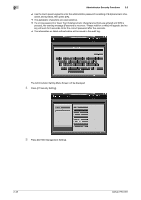
2 2.5.6 Administrator Security Functions 2.5 Analyzing Audit Log Audit log needs to be analyzed by the administrator regularly (once per month), or when the data saved in the machine are illegally accessed or even tampered. The machine is supposed to store up to 750 logs per month. If more than 750 logs are assumed to be stored in a month, carry out the analysis in a shorter period before unanalyzed logs reach that number. 2-52 Audit log information The audit log contains the following information: 1. date/time: registers date and time of the operation that resulted in the creation of a log entry. 2. id: specifies person who made the operation, or subject for security protection. - -1: operation by customer engineer (CE) - -2: operation by the administrator - -3: operation by the unregistered user - Other integer: indicates subjects for security protection, and the following action IDs narrow down the subject for protection. User ID: numbers from 1 to 1000. Secure User ID: numbers from 1 to 99999. 3. action: indicates number that specifies the operation. Refer to the following table for details. 4. result: records result of the operation. For password authentication, success/failure will be indicated as OK/NG. For operations without password authentication, all log entries will be indicated as OK. Table of items saved in audit log No. Operation Audit ID 1 CE authentication CE ID 2 Administrator authentication Administrator ID 3 Set/Change Enhanced Security mode Administrator ID 4 Print audit log CE ID 5 Change/Register CE password CE ID 6 Change/Register administrator pass- CE ID/Administrator ID word 7 Create user by administrator User ID 8 Change/Register user password by ad- User ID ministrator 9 Delete user User ID 10 Change user attribute 11 Password authentication for user User ID User ID*1/Unregistered user ID*2 12 Change attributes of user by user (user User ID password, etc.) 13 Access to file (Read document data) User ID Stored action 01 02 03 04 05 06 Result OK/NG OK/NG OK OK OK OK 07 OK 08 OK 09 OK 10 OK 11 OK/NG 12 OK 13 OK bizhub PRO 951