McAfee MTP10EMB3RAA Processor Guide - Page 52
Emailing and scheduling reports
 |
UPC - 731944587981
View all McAfee MTP10EMB3RAA manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 52 highlights
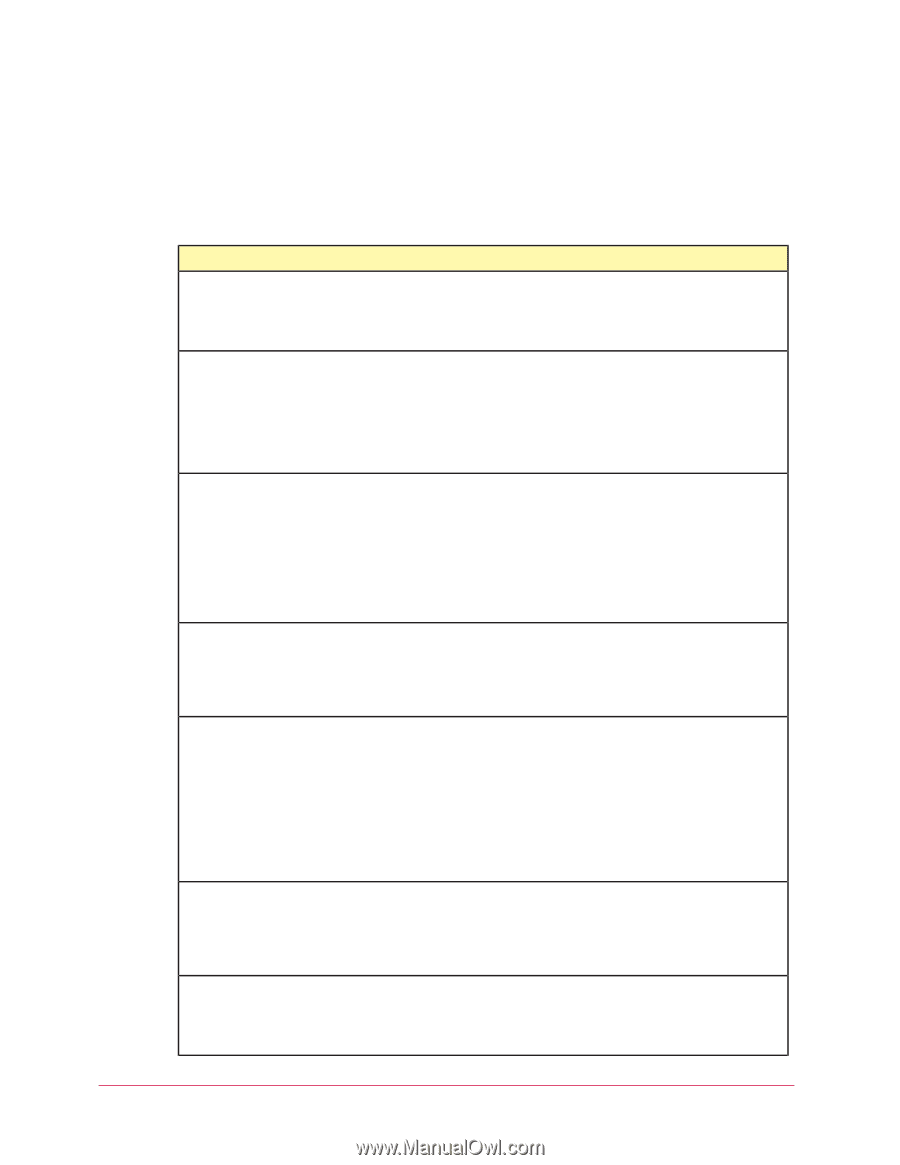
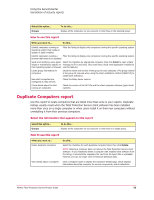
Using the SecurityCenter Generation of security reports Emailing and scheduling reports You can run reports on demand or schedule them to at run regular intervals and then send them as email attachments to one or more recipients. NOTE: For more information about reports for specific types of protection, see the chapters for those types of protection. For versions of Total Protection Service that include vulnerability scanning, reports are available on the vulnerability scanning portal. Use this report... Detections To view... The types of potentially malicious code or unwanted programs that have been found on your network. Use this report to manage detections of viruses and potentially unwanted programs. Unrecognized Programs Programs that spyware protection or firewall protection detected on your network. Use this report to manage your potentially unwanted program detections and Internet applications blocked by firewall protection. You can add approved programs and allowed Internet applications to policies directly from the report. Inbound Events Blocked by Firewall Computers where inbound or outbound communications were blocked by firewall protection. Use this report to manage blocked communications. NOTE: For blocked events to be reported, the Report blocked events option must be enabled in the Firewall Protection policy. Blocked events are logged for all computers that are assigned a policy where this option is enabled. Duplicate Computers Computer Profiles Computers that appear more than once in administrative reports. Use this report to track down obsolete computers and those where Total Protection Service has been incorrectly reinstalled and tracked as multiple installations. For each client computer, the version of the Microsoft Windows operating system and Microsoft Internet Explorer web browser running, which group it belongs to, whether it is configured as a relay server, and other details. Use this report to locate computers where you need to install software patches for a specific browser or operating system, check the version of the client software, identify relay servers, and identify the group number for use in silent installation. Detection History A graphical summary of the number of detections and the number of computers where detections occurred on your network over the past year. Use this report to evaluate the effectiveness of your security strategy. Web Filtering Report A summary of browsing activity on your account. Shows the types of sites that client computers attempted to access by content rating and category. Includes successful, warned, and blocked access attempts. (Available only when web filtering policy options are 52 McAfee Total Protection Service Product Guide