Ricoh Aficio MP 5002 Security Target - Page 25
Scanner Function, Document Server Function and Fax Function by the authorised TOE users who are - scanner driver
 |
View all Ricoh Aficio MP 5002 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 25 highlights
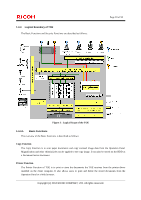
Page 24 of 93 operation on the user documents and user jobs based on the privileges for the user role, or the operation permissions for each user. Use-of-Feature Restriction Function The Use-of-Feature Restriction Function is to authorise the operations of Copy Function, Printer Function, Scanner Function, Document Server Function and Fax Function by the authorised TOE users who are authenticated by Identification and Authentication Function. It authorises the use of functions based on the user role and the operation permissions for each user. Network Protection Function The Network Protection Function is to prevent information leakage through wiretapping on the LAN and detect data tampering. The protection function can be enabled using a Web browser to specify the URL for possible encrypted communication. If the Printer Function is used, the protection function can be enabled using the printer driver to specify encrypted communication. If the folder transmission function of Scanner Function is used, the protection function can be enabled through encrypted communication. If the e-mail transmission function of Scanner Function is used, the protection function can be enabled through encrypted communication with communication requirements that are specified for each e-mail address. If the LAN-Fax Transmission Function of Fax Function is used, the protection function can be enabled using the fax driver to specify encrypted communication. When communicating with RC Gate, encrypted communication is used. Residual Data Overwrite Function The Residual Data Overwrite Function is to overwrite specific patterns on the HDD and disable the reusing of the residual data included in deleted documents, temporary documents and their fragments on the HDD. Stored Data Protection Function The Stored Data Protection Function is to encrypt the data on the HDD and protect the data so that data leakage can be prevented. Security Management Function The Security Management Function is to control operations for TSF data in accordance with user role privileges or user privileges allocated to normal users, MFP administrator, and supervisor. Software Verification Function The Software Verification Function is to verify the integrity of the executable codes of the MFP Control Software and FCU Control Software and to ensure that they can be trusted. Fax Line Separation Function The Fax Line Separation Function is to restrict input information from the telephone lines so that only fax data can be received and unauthorised intrusion from the telephone lines (same as the "fax line") can be prevented. Also, this function can be used to prohibit transmissions of received faxes so that unauthorised intrusion from the telephone lines to the LAN can be prevented. Copyright (c) 2012 RICOH COMPANY, LTD. All rights reserved.