Ricoh Aficio MP 5002 Security Target - Page 73
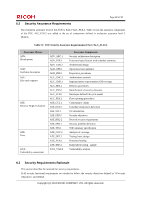
O.FUNC.NO_ALT Protection of user job alteration, O.PROT.NO_ALT Protection of TSF protected data
 |
View all Ricoh Aficio MP 5002 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 73 highlights
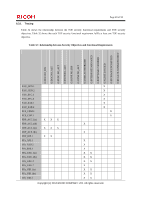
Page 72 of 93 O.FUNC.NO_ALT Protection of user job alteration O.FUNC.NO_ALT is the security objective to prevent the user jobs from unauthorised alteration by persons without a login user name, or by persons with a login user name but without an access permission to the user job. To fulfil this security objective, it is required to implement the following countermeasures. (1) Specify and implement the access control to user jobs. FDP_ACC.1(a) and FDP_ACF.1(a) allow the MFP administrator to delete user jobs, and the normal user with the permission to delete the applicable user job. The supervisor and RC Gate are not allowed to delete user jobs. Deletion is the only modification operation on this TOE's user jobs. (2) Use trusted channels for sending or receiving user jobs. The user jobs sent and received by the TOE via the LAN are protected by FTP_ITC.1. (3) Management of the security attributes. FMT_MSA.1(a) restricts each available operation (newly create, query, modify and delete) for the login user name to specified users only. FMT_MSA.3(a) sets the restrictive value to the security attributes of user jobs (object) when the user jobs are generated. By satisfying FDP_ACC.1(a), FDP_ACF.1(a), FTP_ITC.1, FMT_MSA.1(a) and FMT_MSA.3(a), which are the security functional requirements for these countermeasures, O.FUNC.NO_ALT is fulfilled. O.PROT.NO_ALT Protection of TSF protected data alteration O.PROT.NO_ALT is the security objective to allow only users who can maintain the security to alter the TSF protected data. To fulfil this security objective, it is required to implement the following countermeasures. (1) Management of the TSF protected data. By FMT_MTD.1, only the MFP administrator is allowed to manage the minimum character number for Basic Authentication, password complexity setting for Basic Authentication, Number of Attempts before Lockout for Basic Authentication, settings for Lockout Release Timer for Basic Authentication, lockout time for Basic Authentication, auto logout time of the Operation Panel, date, time, S/MIME user information, destination folder, Stored Reception File User, user authentication method, IPSec setting information, @Remote setting information, and Device Certificate. (2) Specification of the Management Function. FMT_SMF.1 performs the required Management Functions for Security Function. (3) Specification of the roles. FMT_SMR.1 maintains the users who have the privileges. (4) Use trusted channels for sending or receiving the TSF protected data. The TSF protected data sent and received by the TOE via the LAN are protected by FTP_ITC.1. By satisfying FMT_MTD.1, FMT_SMF.1, FMT_SMR.1 and FTP_ITC.1, which are the security functional requirements for these countermeasures, O.PROT.NO_ALT is fulfilled. Copyright (c) 2012 RICOH COMPANY, LTD. All rights reserved.