Cisco CP-7942G Administration Guide - Page 28
Establishing and Identifying Protected Calls, Call Security Interactions and Restrictions
 |
View all Cisco CP-7942G manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 28 highlights
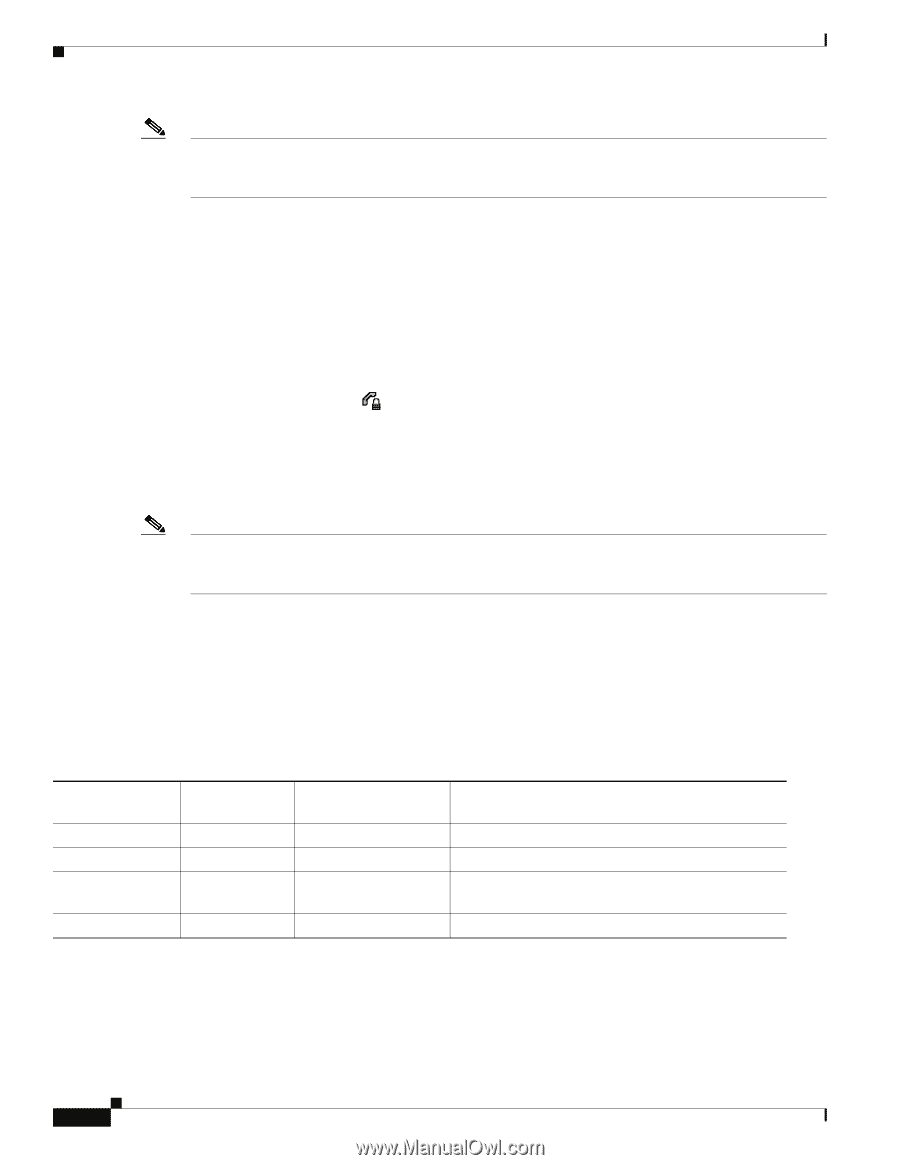
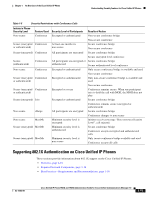
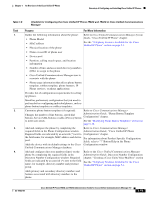
Understanding Security Features for Cisco Unified IP Phones Chapter 1 An Overview of the Cisco Unified IP Phone Note There are interactions, restrictions, and limitations that affect the security level of the conference call depending on the security mode of the participant's phones and the availability of secure conference bridges. See Table 1-4 and Table 1-5 for information about these interactions. Establishing and Identifying Protected Calls A protected call is established when your phone, and the phone on the other end, is configured for protected calling. The other phone can be in the same Cisco IP network, or on a network outside the IP network. Protected calls can only be made between two phones. Conference calls and other multiple-line calls are not supported. A protected call is established using this process: 1. A user initiates the call from a protected phone (protected security mode). 2. The phone displays the icon (encrypted) on the phone screen. This icon indicates that the phone is configured for secure (encrypted) calls, but this does not mean that the other connected phone is also protected. 3. A security tone plays if the call is connected to another protected phone, indicating that both ends of the conversation are encrypted and protected. If the call is connected to a non-protected phone, then the secure tone is not played. Note Protected calling is supported for conversations between two phones. Some features, such as conference calling, shared lines, Extension Mobility, and Join Across Lines are not available when protected calling is configured. Call Security Interactions and Restrictions Cisco Unified Communications Manager checks the phone security status when conferences are established and changes the security indication for the conference or blocks the completion of the call to maintain integrity and also security in the system. Table 1-4 provides information about changes to call security levels when using Barge. Table 1-4 Call Security Interactions When Using Barge Initiator's Phone Security Level Feature Used Non-secure Barge Secure (encrypted) Barge Secure (authenticated) Barge Non-secure Barge Call Security Level Encrypted call Authenticated call Encrypted call Authenticated call Results of Action Call barged and identified as non-secure call Call barged and identified as authenticated call Call barged and identified as authenticated call Call barged and identified as non-secure call Table 1-5 provides information about changes to conference security levels depending on the initiator's phone security level, the security levels of participants, and the availability of secure conference bridges. 1-14 Cisco Unified IP Phone 7962G and 7942G Administration Guide for Cisco Unified Communications Manager 7.0 OL-15483-01