Actiontec GT701D User Manual - Page 42
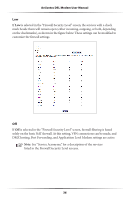
DMZ Hosting
 |
View all Actiontec GT701D manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 42 highlights
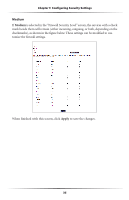
Chapter 5 Configuring Security Settings For multiple ports: 1. Enter the rule name in the "Rule Name" text box. The name is usually based on the application or game title. 2. Set "Protocol" to "TPC." 3. Enter the starting port number of the port range in the "Port Start" and "Port Map Start" text boxes, and the last port of the range in the "Port End" text box. For example, if the port range is 5000 to 6000, enter "5000" in the "Port Start" and "Port Map Start" text boxes, and "6000" in the "Port End" text box. 4. Click Apply. 5. Change Protocol to "UDP." 6. Enter the port numbers again, as in step 3. 7. Click Apply again. The rule's TPC and UDP mapping appear at the bottom of the screen. 8. Click Back. 9. Select the computer on which to open the ports, then click User. 10. Select the rule, then click Add to move the rule to the "Applied Rule" text box. 11. Click Apply. DMZ Hosting Selecting DMZ Hosting in the "Security" screen generates the "DMZ Hosting" screen. To use DMZ hosting, select the computer on the network to be used as a DMZ host in the "DMZ Host PC Name" drop-down menu, then click On. 39