Asus P5Q3 Deluxe WiFi-AP n User Manual - Page 38
Setting up wireless security
 |
View all Asus P5Q3 Deluxe WiFi-AP n manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 38 highlights
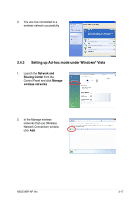
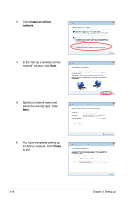
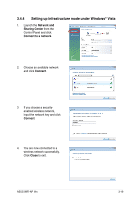
3.5 Setting up wireless security To protect your wireless network, you need to setup a security mechanism on your WiFi-AP @n. Network authentication Network authentication uses certain types of mechanism to identify authenticated wireless clients. WiFi-AP @n supports the following authentication methods: Open system: This option disables authentication protection for your wireless network. Under the Open mode, any IEEE802.11b/g wireless client can connect to your wireless network. Shared key: Shared means using the same WEP keys for authentication and encryption. WPA-PSK WPA-PSK (Pre-Shared Key) is the solution for home and SOHO users who have no 802.11X authentication server within the LAN. To setup WPA-PSK, you need to input a passphrase and let the system generate the key. Combination of letters, numbers and non-alphnumeric charecters is recommended for ensuring security. WPA2-PSK WPA2 (WI-FI Protected Access 2) provides network administrators with a high level of assurance that only authorized users can access the network. Based on the ratified IEEE 802.11i standard, WPA2 provides government grade security. The WPA2 can be enabled in two versions -WPA2-Personal and WPA2-Enterprise. WPA2-Personal protects unauthorized network access by utilizing a set-up password. WPA2-Enterprise verifies network users through a server. WPA2 is backward compatible with WPA. Encryption Encryption is used to convert plain text data into unreadable codes with certain type of algorithm before capsulation for wireless transmission. WiFi-AP @n supports the following encryption methods: WEP: TKIP: AES WEP stands for Wired Equivalent Privacy. It uses 64 or 128-bit static keys. You can let the system generate the WEP keys by inputting a Passphrase. Temporal Key Integrity Protocol (TKIP) dynamically generates unique keys to encypt every data packet in a wireless session. Advanced Encryption Standard (AES) is a dependable encryption adopted in WPA2 or IEEE802.11i standard. It offers stronger protection and greatly increases the complexity of wireless encryption. 3-20 Chapter 3: Setting up