D-Link DGS-3620-28TC-SI Product Manual - Page 346
IP-MAC-Port Binding (IMPB), IMPB Global Settings
 |
View all D-Link DGS-3620-28TC-SI manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 346 highlights
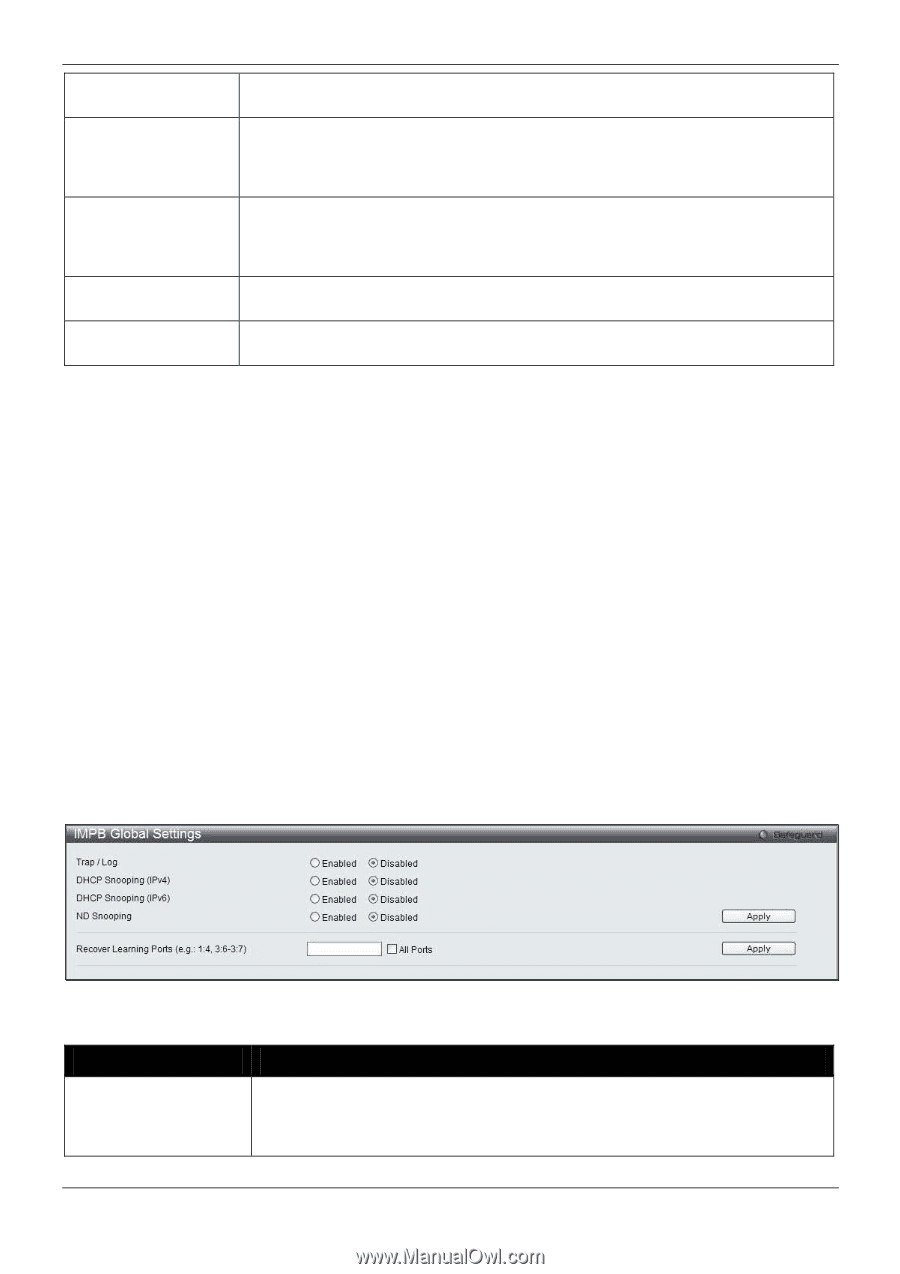
xStack® DGS-3620 Series Managed Switch Web UI Reference Guide BadAuthenticators The number of RADIUS Accounting-Response packets, which contained invalid authenticators, received from this server. PendingRequests The number of RADIUS Accounting-Request packets sent to this server that have not yet timed out or received a response. This variable is incremented when an Accounting-Request is sent and decremented due to receipt of an AccountingResponse, a timeout or a retransmission. Timeouts The number of accounting timeouts to this server. After a timeout the client may retry to the same server, send to a different server, or give up. A retry to the same server is counted as a retransmit as well as a timeout. A send to a different server is counted as an Accounting-Request as well as a timeout. UnknownTypes The number of RADIUS packets of unknown type which were received from this server on the accounting port. PacketsDropped The number of RADIUS packets, which were received from this server on the accounting port and dropped for some other reason. Click the Clear button to clear the current statistics shown. IP-MAC-Port Binding (IMPB) The IP network layer uses a IPv4/IPv6 address. The Ethernet link layer uses a MAC address. Binding these two address types together allows the transmission of data between the layers. The primary purpose of IP-MAC-port binding is to restrict the access to a switch to a number of authorized users. Authorized clients can access a switch's port by either checking the pair of IP-MAC addresses with the pre-configured database or if DHCP snooping has been enabled in which case the switch will automatically learn the IP/MAC pairs by snooping DHCP packets and saving them to the IMPB white list. If an unauthorized user tries to access an IP-MAC binding enabled port, the system will block the access by dropping its packet. For the xStack® DGS-3620 series of switches, active and inactive entries use the same database. The maximum number of IPv4/IPv6 entries is 510/511. The creation of authorized users can be manually configured by CLI or Web. The function is port-based, meaning a user can enable or disable the function on the individual port. IMPB Global Settings Users can enable or disable the Trap/Log State and DHCP Snoop state on the Switch. The Trap/Log field will enable and disable the sending of trap/log messages for IP-MAC-port binding. When enabled, the Switch will send a trap message to the SNMP agent and the Switch log when an ARP/IP packet is received that doesn't match the IP-MAC-port binding configuration set on the Switch. To view this window, click Security > IP-MAC-Port Binding (IMPB) > IMPB Global Settings as shown below: Figure 8-26 IMPB Global Settings The fields that can be configured are described below: Parameter Description Trap / Log Click the radio buttons to enable or disable the sending of trap/log messages for IPMAC-port binding. When Enabled, the Switch will send a trap message to the SNMP agent and the Switch log when an ARP/IP packet is received that doesn't match the IP-MAC-port binding configuration set on the Switch. The default is Disabled. 336