Dell Powerconnect W-ClearPass Virtual Appliances W-ClearPass Policy Manager 6. - Page 94
No Action, Do SNMP bounce, Trigger RADIUS CoA action, Profiler, Authorization, Service, Roles
 |
View all Dell Powerconnect W-ClearPass Virtual Appliances manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 94 highlights
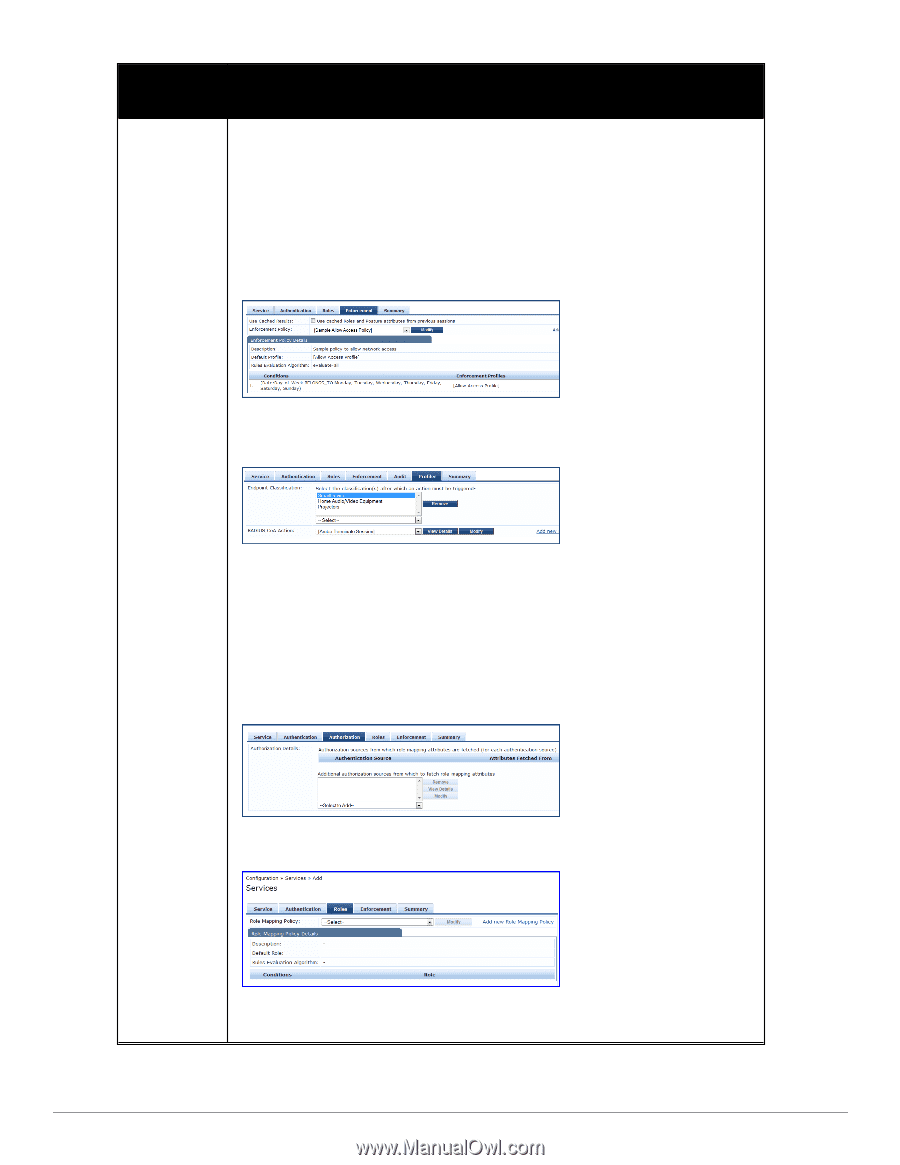
Service Type Description/ Available Policy Components (in tabs)/ Service Rule (in Rules Editor)/ Service-specific policy components (called out with legend below) l No Action: The audit will not apply policies on the network device after this audit. l Do SNMP bounce: This option will bounce the switch port or to force an 802.1X reauthentication (both done via SNMP). NOTE: Bouncing the port triggers a new 802.1X/MAC authentication request by the client. If the audit server already has the posture token and attributes associated with this client in its cache, it returns the token and the attributes to Policy Manager. l Trigger RADIUS CoA action: This option sends a RADIUS Change of Authorization command to the network device by Policy Manager. You must select an enforcement policy (see "Configuring Enforcement Policies " on page 229) for a service. Optionally configure Profiler settings. Select one or more Endpoint Classification items from the drop down list, then select the RADIUS CoA action. You can also create a new action by selecting the Add new RADIUS CoA Action link. To create an authorization source for this service click on the Authorization tab. This tab is not visible by default. To enable Authorization for this service select the Authorization check box on the Service tab. Policy Manager fetches role mapping attributes from the authorization sources associated with service, regardless of which authentication source was used to authenticate the user. For a given service, role mapping attributes are fetched from the following authorization sources: l The authorization sources associated with the authentication source l The authorization sources associated with the service. For more information on configuring authorization sources, refer to "Adding and Modifying Authentication Methods" on page 111. To associate a role mapping policy with this service click on the Roles tab. For information on configuring role mapping policies, refer to "Configuring a Role Mapping Policy " on page 154. By default, this type of service does not have Posture checking enabled. To enable posture checking for this service select the Posture Compliance check box on the Service tab. 94 Dell Networking W-ClearPass Policy Manager 6.0 | User Guide