HP Jetdirect 610n HP Jetdirect Print Servers - HP Jetdirect and SSL/TLS - Page 12
Public Key Infrastructure and Public Key Certificate Basics - drivers
 |
View all HP Jetdirect 610n manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 12 highlights
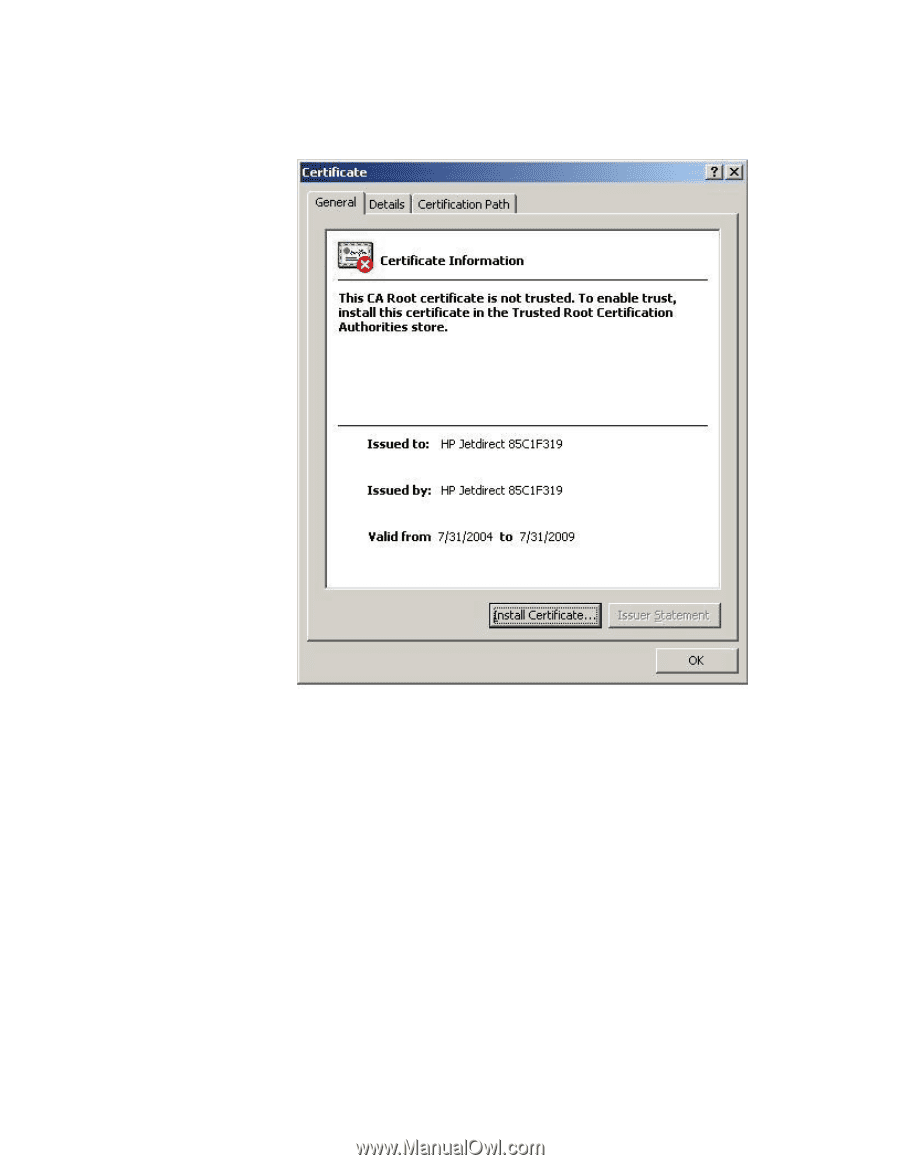
Public Key Infrastructure and Public Key Certificate Basics Let's go back to the certificate information dialog, shown in Figure 14: Figure 14 - Certificate Information Here is the message: "This CA Root certificate is not trusted." To enable trust, install this certificate in the Trusted Root Certification Authorities store". What the message is trying to say is that "HP Jetdirect 85C1F319", who issued the certificate "HP Jetdirect 85C1F319", is not trusted. Because the "Issued by:" name is the same as the "Issued to:" name, this is a self-signed certificate. The Security Alert dialog is troubling because it is indicative of a trust problem. In the terms of our analogy, it would be like a driver, who has been pulled over by the Highway Patrol, handing the officer a driver's license that the driver has created for himself indicating that he has the privilege to drive in the state. The Highway Patrol would obviously not trust it and unfortunately may not consider it a laughing matter. In essence, a digital certificate, one used by computers, binds an identity to a key and needs to be issued by a trusted third party. What is a key? A key is a secret that is used in cryptographic algorithms. There are public keys and private keys used for asymmetric cryptography and symmetric keys used for symmetric cryptography. Let's look at symmetric cryptography first. 12