HP Jetdirect 610n HP Jetdirect Print Servers - HP Jetdirect and SSL/TLS - Page 77
SSL/TLS Client: Understanding Certificate Chains
 |
View all HP Jetdirect 610n manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 77 highlights
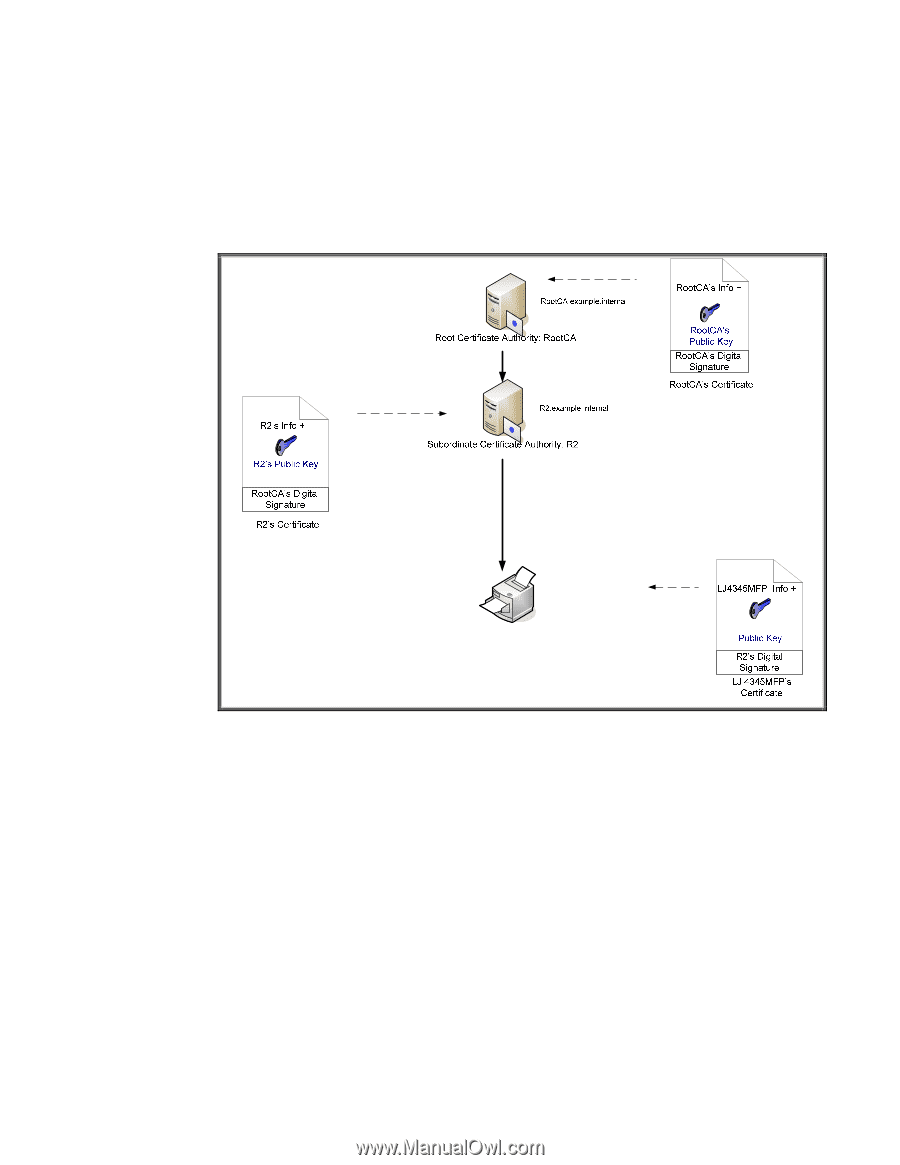
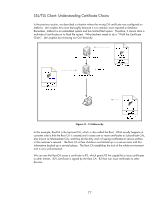
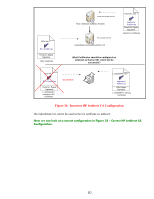
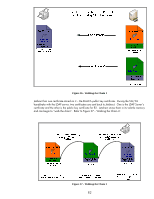
SSL/TLS Client: Understanding Certificate Chains In the previous section, we described a situation where the wrong CA certificate was configured on Jetdirect. Let's explain this more thoroughly because it is a common issue reported on Jetdirect. Remember, Jetdirect is an embedded system and has limited flash space. Therefore, it cannot store a multitude of certificates on its flash file system. What Jetdirect needs to do is "Walk the Certificate Chain". Let's explain by reviewing our CA Hierarchy. Figure 31 - CA Hierarchy In this example, RootCA is the top level CA, which is also called the Root. What usually happens at customer sites is that the Root CA is created and it issues one or more certificates to Subordinate CAs, also known as Intermediate CAs, and they do the dirty work of issuing certificates to various entities in the customer's network. The Root CA is then shutdown and locked up in a secure room with this information backed up in several places. The Root CA establishes the trust of the whole environment and is very well protected. We can see that RootCA issues a certificate to R2, which grants R2 the capability to issue certificates to other entities. R2's certificate is signed by the Root CA. R2 then can issue certificates to other devices. 77