HP Jetdirect 610n HP Jetdirect Print Servers - HP Jetdirect and SSL/TLS - Page 83
SSL/TLS Client: Certificates and Name Verification
 |
View all HP Jetdirect 610n manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 83 highlights
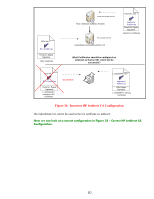
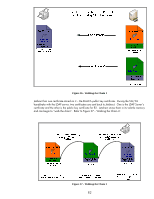
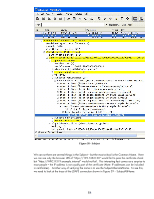
Jetdirect verifies that R2 has signed the server's certificate. It also verifies R2's certificate (e.g., it has not expired and so on) and makes sure that R2's certificate was signed by RootCA. This "walking the chain" functionality is very important for devices with limited storage space for certificates - like HP Jetdirect. SSL/TLS Client: Certificates and Name Verification You may remember that having "https://192.168.0.20" in the URL of the browser resulted in Internet Explorer 7 reporting a certificate problem but that "https://NPIC1F319.example.internal" ended up with everything okay. How the SSL/TLS client authenticates the SSL/TLS server is very important and is unfortunately mired in practical deployment problems. We'll try to sort through it all! The certificate itself has two very important fields that need to be discussed • Subject • SubjectAltName The subject field is where the Common Name is stored. What is the Common Name? Well, that is a good question since it was never really properly defined. The most likely thing for HTTPS is that it is the Fully Qualified Domain Name. Let's look at a trace where a browser has established an HTTPS connection with the Jetdirect device. Refer to Figure 38 - Subject. 83