HP Jetdirect 610n HP Jetdirect Print Servers - HP Jetdirect and SSL/TLS - Page 26
Using HTTPS with HP Jetdirect
 |
View all HP Jetdirect 610n manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 26 highlights
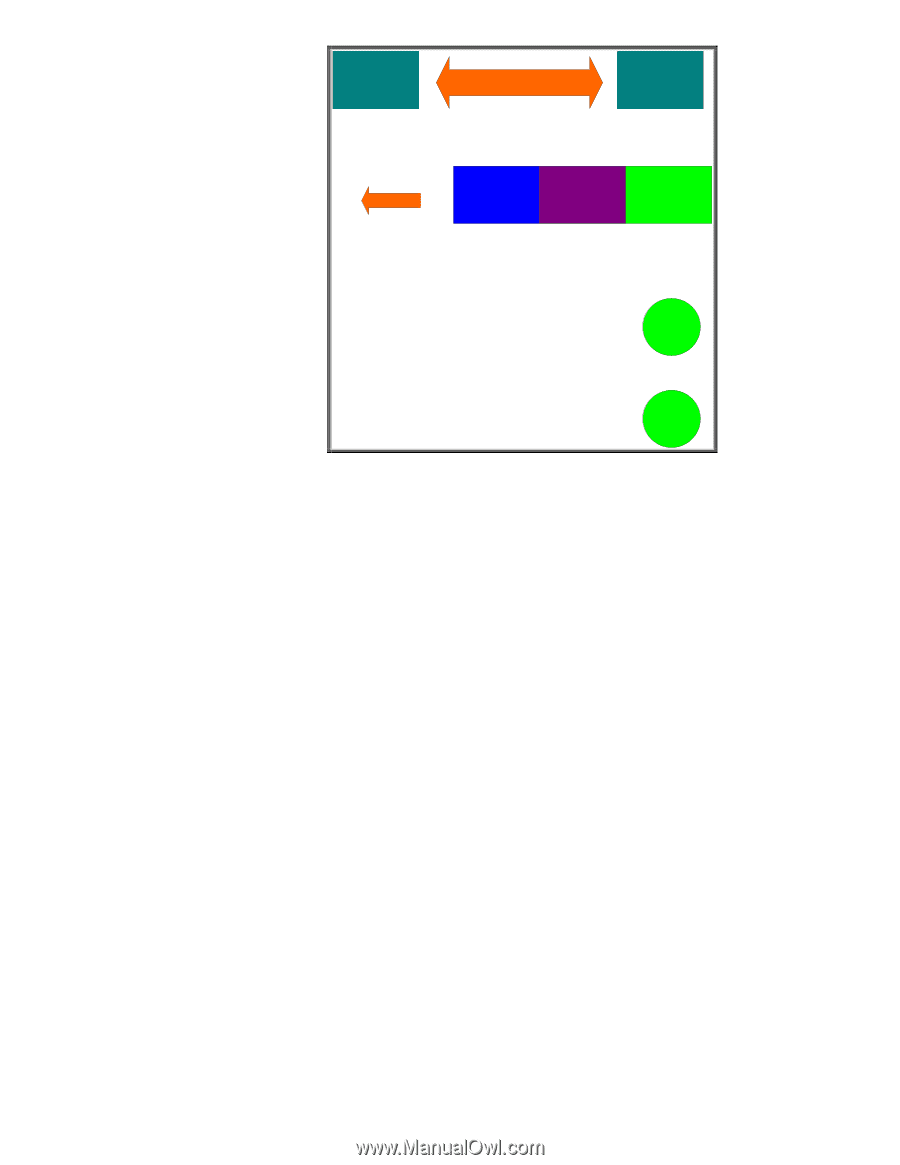
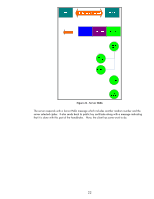
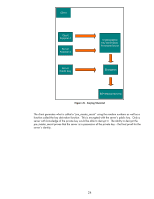
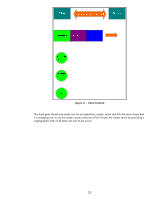
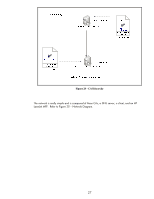
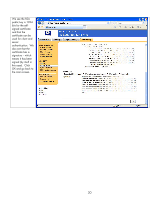
Client TCP Connection Established Server TCP SSL Record Handshake Change Cipher Spec Finished Figure 28 - Server Finished The server decrypts the pre_master_secret and generates the master_secret. It goes ahead and let's the client know that it is changing over to use the master_secret and proves that it knows the master secret by providing a cryptographic hash of all data sent over to the client. Once the client and server both verify the cryptographic hashes, the handshake process is done and actual client data can be sent over the SSL/TLS connection. Let's see how SSL/TLS works in its most popular form: HTTPS. Using HTTPS with HP Jetdirect Before we begin, we need a little info on the setup. We have a RootCA with a subordinate CA called R2. The subordinate CA issues certificates to clients on the network. Refer to Figure 29 - CA Hierarchy. 26