Cisco SLM2008 Administration Guide - Page 32
Security, Configuring 802.1X Settings - radius
 |
UPC - 745883579969
View all Cisco SLM2008 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 32 highlights
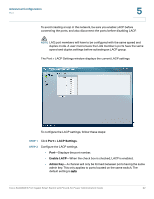
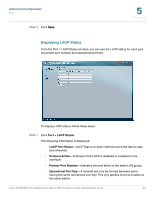
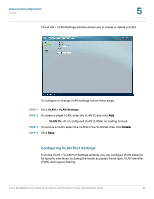
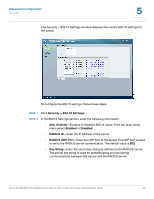
Advanced Configuration Security 5 forwarded to the VLAN based on the PVID of its ingress port. All frame types are selected by default. • PVID (Port VLAN identifier)-VLAN ID assigned to untagged frames received on the interface. The default value is 1. For all other VLANs, an interface must first be configured as an untagged member before you can assign its PVID to that group. STEP 3 Click Save. Security This section describes how to configure the security settings for the switch. • Configuring 802.1X Settings, page 27 • Configuring 802.1X Parameter, page 30 • Configuring Static MAC Address, page 32 • Configuring Management Access List, page 33 • Configuring Storm Control, page 34 Configuring 802.1X Settings Network switches can provide open and easy access to network resources by simply attaching a client PC. Although this automatic configuration and access is a desirable feature, it also allows unauthorized personnel to easily intrude and possibly gain access to sensitive network data. The IEEE 802.1X (dot1X) standard defines a port-based access control procedure that prevents unauthorized access to a network by requiring users to first submit credentials for authentication. Access to all switch ports in a network can be centrally controlled from a server, which means that authorized users can use the same credentials for authentication from any point within the network. The Cisco SLM2008 switch uses the Extensible Authentication Protocol over LANs (EAPOL) to exchange authentication protocol messages with the client, and a remote RADIUS authentication server to verify user identity and access rights. When a client connects to a switch port, the switch responds with an EAPOL identity request. The client provides its identity (such as a user name) in an EAPOL Cisco SLM2008 8-Port Gigabit Smart Switch with PD and AC Power Administration Guide 27