Compaq 307560-001 Compaq Enterprise Security Framework
Compaq 307560-001 - ProLiant - 2500R Manual
 |
UPC - 743172470379
View all Compaq 307560-001 manuals
Add to My Manuals
Save this manual to your list of manuals |
Compaq 307560-001 manual content summary:
- Compaq 307560-001 | Compaq Enterprise Security Framework - Page 1
balanced hardware/software solution, and interoperablity with current security at multiple platform levels to clarify security solutions. Through use of The Compaq Enterprise Security Framework, you can develop solutions that do not compromise performance yet are still pragmatic and easy to use. In - Compaq 307560-001 | Compaq Enterprise Security Framework - Page 2
quality or correctness, nor does it ensure compliance with any federal, state or local requirements. Compaq does not warrant products other than its own strictly as stated in Compaq product warranties. Product names mentioned herein may be trademarks and/or registered trademarks of their respective - Compaq 307560-001 | Compaq Enterprise Security Framework - Page 3
of over $100 million. While most security problems remain basic, such as viruses, password managers must design a practical roadmap to guide their enterprises through this tangle of information, that meets their business requirements. Compaq's Enterprise Security Framework delivers the critical - Compaq 307560-001 | Compaq Enterprise Security Framework - Page 4
WHITE PAPER (cont.) ... SECURITY ENVIRONMENT Computing security has always been critical to enterprises. However, in today's environment the components of the computing world have changed in ways that make computing security more critical and complex. In the past, computing security focused on - Compaq 307560-001 | Compaq Enterprise Security Framework - Page 5
WHITE PAPER (cont.) ... residing on mainframes and mid-range systems in a closely monitored and physically secure environment - the glass house. In this setting, businesses deployed private, leased lines for external data transactions with known partners and used e-mail for internal communication - Compaq 307560-001 | Compaq Enterprise Security Framework - Page 6
under-price their product in the market). By the same token, crashing a rival's critical systems can hurt their reputation for customer service or on-time performance. Competitors can also create a competitive advantage through the impact of a publicized breach on the market position and perception - Compaq 307560-001 | Compaq Enterprise Security Framework - Page 7
WHITE PAPER (cont.) ... The other potential "unfriendly" force is government. Government regulation of computing security is still evolving; however, it is possible that both the state and federal governments may begin to hold enterprises responsible for the privacy of consumer information. - Compaq 307560-001 | Compaq Enterprise Security Framework - Page 8
parts directly, manufacturers and suppliers reduce their customer service costs. Security Environment: Current Situation Over the the information and applications on these devices are far more valuable. The problem is widespread. As mentioned earlier, over 75% of the businesses surveyed reported - Compaq 307560-001 | Compaq Enterprise Security Framework - Page 9
WHITE PAPER (cont.) ... nature of some attacks, and because digital material can be copied without any evidence of access or theft. In addition, most computer crimes and security incidents go unreported because businesses are unwilling to reveal the weaknesses of their computer systems to outsiders - Compaq 307560-001 | Compaq Enterprise Security Framework - Page 10
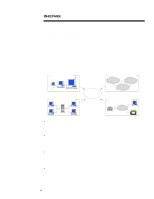
single users on the device, those serving groups of internal network users, or those serving users across the Externet). Using these terms, Compaq's enterprise customers can better understand the market for security products and easily map out the solutions they require. Defining the objectives of - Compaq 307560-001 | Compaq Enterprise Security Framework - Page 11
in consulting and security testing firms is crucial to large enterprises; these services are projected to grow into a $5 billion market by the year devices (e.g., power-onpasswords, physical locks, virus scanning, file encryption). Internal Network Implementation Internal Network solutions protect - Compaq 307560-001 | Compaq Enterprise Security Framework - Page 12
measures, parties may use this station as a launching pad for attacks on local network services that trust the identity of individual devices. Similarly, a client that trusts the identity of networked services is vulnerable to attacks from the network. Some solutions, however, can protect different - Compaq 307560-001 | Compaq Enterprise Security Framework - Page 13
implications of critical market trends on their purchasing decisions. Compaq has identified four key computing security trends that have important Authorization/ Access Control Privacy Integrity Firewall Base Firewall Web filter Support for VPN, secure remote access APIs for new applications - Compaq 307560-001 | Compaq Enterprise Security Framework - Page 14
third party solutions. The most aggressive effort to date is from CheckPoint, whose OPSEC architecture supports major existing standards such as IPSEC, LDAP, etc., and offers API support for multiple solutions such as access control, address translation, virus scanning, and activity monitoring. The - Compaq 307560-001 | Compaq Enterprise Security Framework - Page 15
applications. The certificate infrastructure and technology is still developing. Certificate server products are still in development and Certificate Authority services are in their infancy. For example, Secure Electronic Transactions (SET), the new E-Commerce credit card protocol, will depend - Compaq 307560-001 | Compaq Enterprise Security Framework - Page 16
public-key encryption operations per transaction, potentially slowing existing servers to a crawl. Specialized hardware will be necessary to alleviate this problem. In addition, smartcards and tokens can provide robust, high-performance encryption solutions on the desktop, and can be used as - Compaq 307560-001 | Compaq Enterprise Security Framework - Page 17
Cylink Entrust Hardware Auditing/Management Haystack ISS Software Figure 12 Services Cross-vendor usage, ease of use, interoperability, and practical applicability remain crucial issues. Firewalls provide some examples of the problems around ease of use and interoperability. While the industry - Compaq 307560-001 | Compaq Enterprise Security Framework - Page 18
deployment of enterprise security, Compaq has developed the Enterprise Security Framework. Using this framework, Compaq's enterprise customers can get of attacks it protects against (e.g., impersonation, denial of service, theft) and the security objectives served (inter-enterprise communications - Compaq 307560-001 | Compaq Enterprise Security Framework - Page 19
transparent to appropriate users. Offers easy to use administration tools. Offers centralized, seamless administration for internal network, and Externet security services. Easy to manage; Enterprise can flexibly build/change solutions to meet their needs. Based on open standards. In practice - Compaq 307560-001 | Compaq Enterprise Security Framework - Page 20
security measures • Strong two faction local • Very strong file and drive identification and access control privacy solution, using software multiple • Basic ACLs, embedded in robust security services of security services with centralized management network operating system • Centralized - Compaq 307560-001 | Compaq Enterprise Security Framework - Page 21
integrate the solutions, and provide a manageable, secure computing environment. Guided by our customers' requirements, our strategy is as follows: • with capacity planning information. • Explore the opportunity for Compaq to build hardware and software security solutions that address both

W
HITE
P
APER
248A/0897ECG
1
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
August 1997
Prepared By
Internet Solutions
Business Unit
Compaq Computer
Corporation
C
ONTENTS
Introduction
................
3
Security
Environment
................
4
Security Environment:
Importance and Trends
.....
4
Security Environment:
Threats and Pressures
......
5
Security Environment:
Enterprise Opportunities/
Risks
................................
7
Security Environment:
Current Situation
..............
8
Understanding
Security
.....................
10
Security Market
.........
13
Security Market: Firewall
Expansion
......................
13
Security Market:
Identification and
Authentication
Importance
.....................
14
Security Market:
Balanced Hardware/
Software Solutions
..........
15
Security Market:
Proliferation/Limitation of
Security Offerings
...........
16
Enterprise Security
Framework
................
18
Conclusion
................
21
Compaq Enterprise Security
Framework
In the highly competitive world of enterprise computing, security has become an intricate
and critical element. The Compaq Enterprise Security Framework incorporates the latest
technology, a balanced hardware/software solution, and interoperablity with current
security at multiple platform levels to clarify security solutions. Through use of The
Compaq Enterprise Security Framework, you can develop solutions that do not
compromise performance yet are still pragmatic and easy to use. In so doing, you can
help to determine a practical roadmap for the deployment of enterprise security.