Compaq 307560-001 Compaq Enterprise Security Framework - Page 18
Enterprise Security Framework
 |
UPC - 743172470379
View all Compaq 307560-001 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 18 highlights
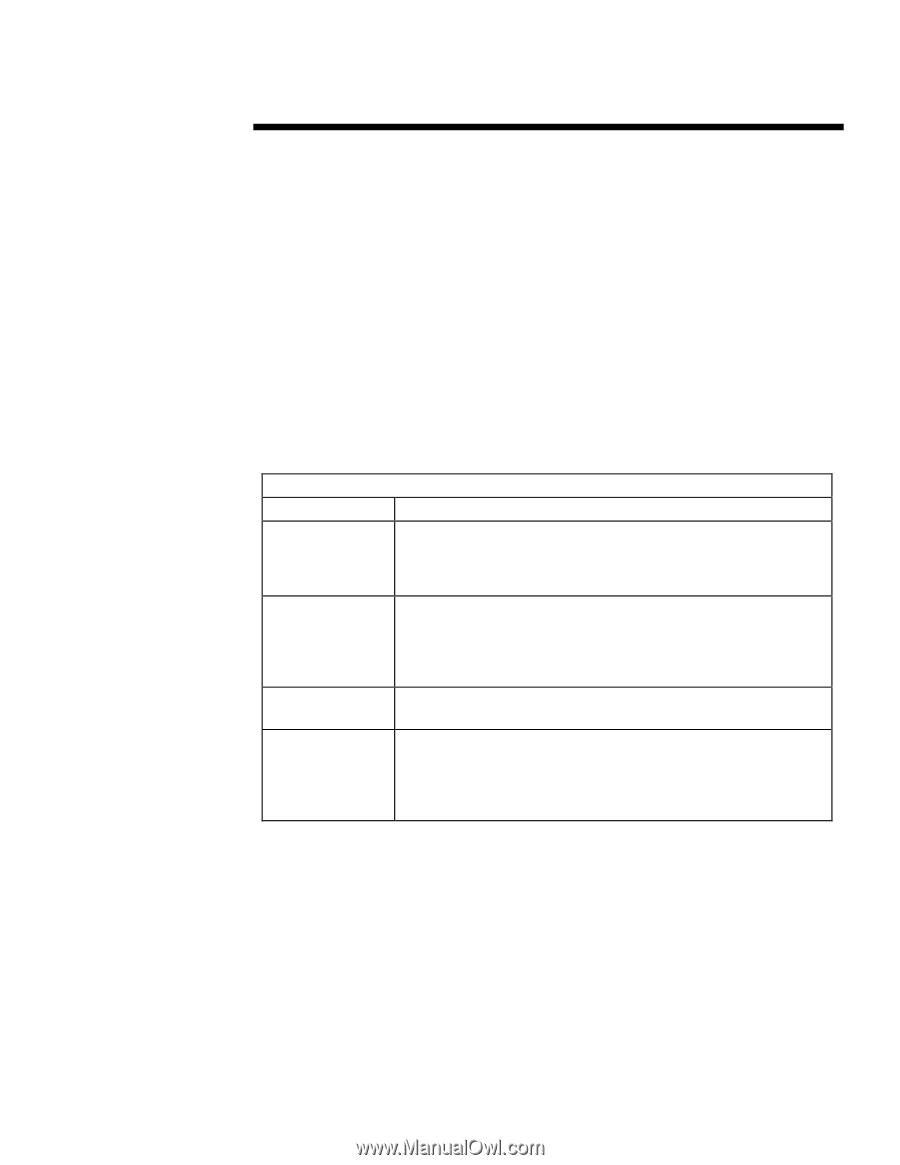
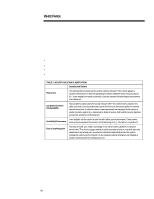
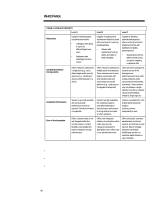
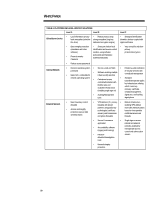
WHITE PAPER (cont.) ... ENTERPRISE SECURITY FRAMEWORK To clarify security solutions and determine a practical roadmap for the deployment of enterprise security, Compaq has developed the Enterprise Security Framework. Using this framework, Compaq's enterprise customers can get a birds-eye view of the security market, judge the suitability of a solution set, and develop both short- and long-term deployment strategies for their enterprise security requirements. The foundation of the security framework is the criteria set it uses to classify security solutions (see Table 2). The framework gauges these solutions relative to: • Robustness. • Comprehensiveness. • Performance. • Manageability. TABLE 2: SECURITY SOLUTION CLASSIFICATION Security Level Criteria Robustness How sophisticated an attack can the security solutions withstand? This criterion gauges a solution's effectiveness in determining/repelling the efforts of different levels of security attacks (i.e., those ranging from casual to planned). It can also measure the technological advancement of a solution set. Comprehensiveness/ Interoperability How complete a solution does the security measure offer? This criterion rates a solution set's ability to provide a security solution that extends from the local client/server platform to external network interactions. A solution's relative comprehensiveness can be judged by the variety of attacks it protects against (e.g., impersonation, denial of service, theft) and the security objectives served (inter-enterprise communications). How "available" will the solution be and how will it affect system performance? These criteria Availability/Performance measure how transparent the execution of the technology is (e.g., how fast is it in operation?). Ease of Use/Integration How easy to install, use, modify, and manage is the solution within a platform or enterprise environment? This criterion gauges whether a solution provides security in a way that users and administrators will actually use, as well as the centralized administration tools they need to manage the solution over the long term. It also measures whether enterprises can integrate a solution seamlessly with the existing product set. Each of these criteria is a critical determinant of how effective or appropriate a solution may be to an individual enterprise. The Enterprise Security Framework establishes "levels" of security based on these criteria, which begin to shape a conceptual roadmap for enterprise security (see Table 3). Each level describes a solution based on how it performs against the above criteria. As solutions move up levels, from A to B to C, these solution sets become sounder and more comprehensive, perform more consistently, and are easier to use. Enterprises may choose the level of security (and thereby the solutions) appropriate to their needs. 18