Compaq 307560-001 Compaq Enterprise Security Framework - Page 4
Security Environment: Importance and Trends - custom
 |
UPC - 743172470379
View all Compaq 307560-001 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 4 highlights
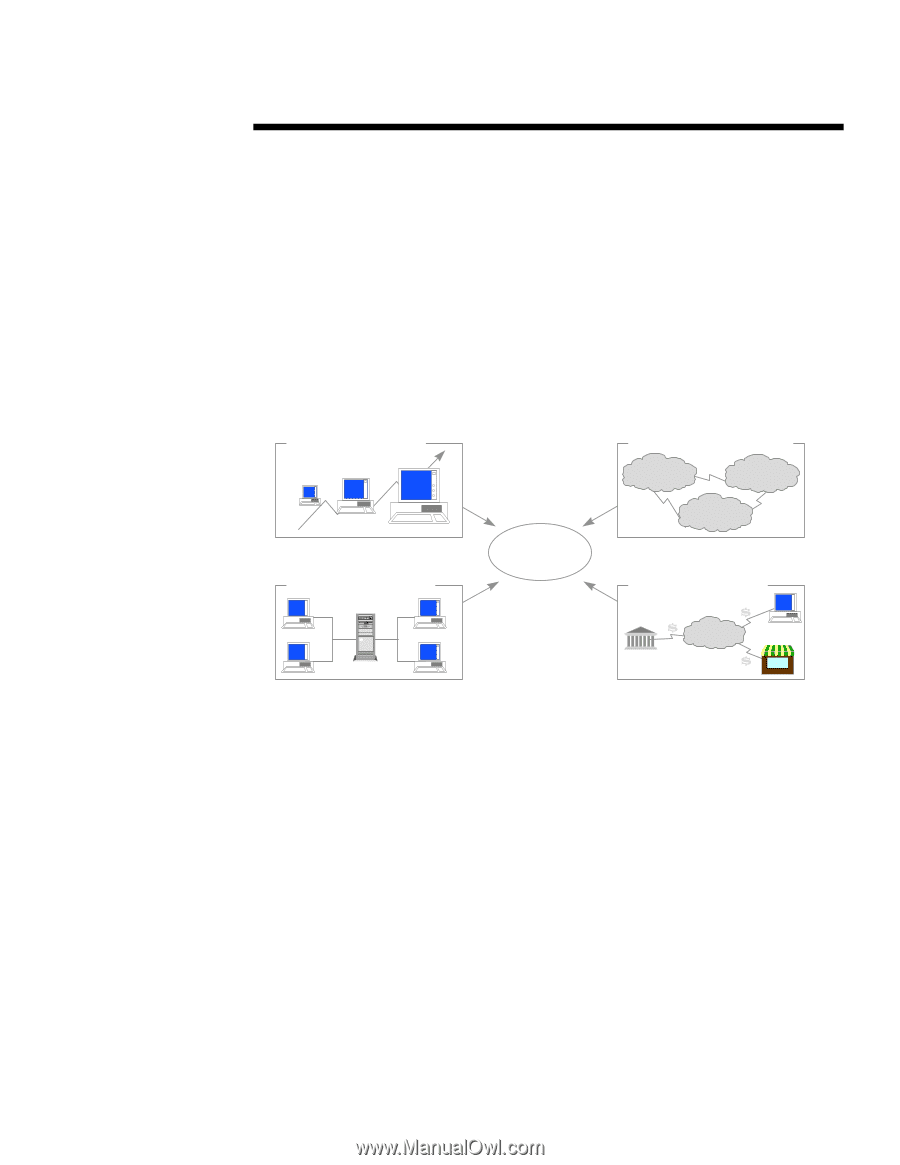
WHITE PAPER (cont.) ... SECURITY ENVIRONMENT Computing security has always been critical to enterprises. However, in today's environment the components of the computing world have changed in ways that make computing security more critical and complex. In the past, computing security focused on protecting assets in a mainframeoriented system. In the current, inter-networked environment, enterprises view security as crucial for two reasons: first, computing security measures protect against potentially devastating losses; and second, security enables businesses and opportunities to generate new revenue and reduce costs. Facing a growing variety of threats, losses, and intense market pressures, IT managers will propel the demand for practical, sound security solutions in the near future. Security Environment: Importance and Trends Several computing environment trends have changed the nature and challenges of computing security (see Figure 1). Computing Growth Internetworked Systems Network A Network B Networked Computing Computing Resources Security Network C Electronic Commerce Public Network Figure 1 • The most obvious computing trend affecting security concerns is the dramatic growth in the installed base of desktops, workstations, laptops, and PDAs in both the consumer and business markets. The simple impact of this growth has been to place more valuable enterprise, personal information, applications, and hardware assets in the hands of numerous people. • The next trend is the importance of networked (client/server) computing, primarily in enterprises and small businesses. As this type of computing has become the dominant architecture, more people have networked access to significant enterprise information and applications than ever before. Some analysts estimate that 50% of the world's computers are networked in some way (LAN, WAN, etc.). • The third trend is the emergence of inter-networked computing. In the last 2-3 years, more enterprises and institutions have connected from their internal networks to the greater networks of other businesses and consumers on the Internet. Inter-connected networks now enable more parties (business partners, customers, and employees) to gain access to crucial systems' resources across public, traditionally unsecured networks. • Finally, the promise of Electronic Commerce is pressing businesses and computing vendors to find ways to securely conduct commercial and private transactions over public networks. In many cases, these transactions involve parties with whom they have no previous affiliation. Together, these trends have created a significantly different and more difficult computing environment for IT managers to secure. Previously, they could control the enterprise's information 4