Compaq 307560-001 Compaq Enterprise Security Framework - Page 6
Enterprise IT, Managers
 |
UPC - 743172470379
View all Compaq 307560-001 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 6 highlights
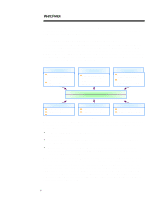
WHITE PAPER (cont.) ... • Thieves can steal corporate laptops for their information and hardware value and sell assets to third parties (i.e. competitors). • Physical security of home PCs is at risk from theft, and data stored on disks is at risk from viral attack. In addition to their responsibility to protect hardware, software, and information assets from these threats, IT managers also face pressures to deploy advanced security to their networks. These pressures can be roughly grouped into "friendly" and "unfriendly" forces (see Figure 3). "FRIENDLY" Consumers, Customers, Partners - Security Pressures - "UNFRIENDLY" Competitors, Government We want to trust you." n Private Information n Joint Plans Enterprise IT Managers "If they can't trust you, there will be costs" n Security as competitive advantage n Supplier data/forecasts Figure 3 n Downstream liability The "friendly" pressures primarily come from customers, consumers, and business partners. Both customers and consumers are concerned with the protection of the private information they share with companies (i.e., medical records, credit card numbers, joint plans). In addition, they are unwilling to participate in E-Commerce with companies until they feel the transactions are completely secure. Business partners' concerns are focused on two areas: first, on achieving a comfortable level of security for companies exchanging information over open "Externets"(meaning the Internet, when it is used for business to business commerce) and secondly, on the question of legal liability, which is brought into focus by the security issue. Recent court cases suggest that there is an emerging precedent of "downstream liability." This precedent requires companies to employ "reasonable measures" of security or face potential liability for computer attacks launched on other parties from within their network (e.g. a criminal breaks into the inadequate security of Company B and uses this trusted position to hack into Business Partner C's more robust security system). When enterprises do not adequately secure their networks, "unfriendly" forces such as competitors and government either take advantage of that deficiency or demand retribution. The first of these forces is competitors. Competitors can turn a company's security weaknesses into an advantage in one or both of two ways: initially, through the competitor-organized theft of information or hindrance of internal systems (i.e. attacks which crash strategic company systems such as call centers, web servers, etc.), and secondly if a competitor accesses or copies private information, they can quickly counter a business' strategies (e.g. beat their competitive bid for work, under-price their product in the market). By the same token, crashing a rival's critical systems can hurt their reputation for customer service or on-time performance. Competitors can also create a competitive advantage through the impact of a publicized breach on the market position and perception of a company. In many security-sensitive industries (e.g. health care, banking), the security of a company's network is a crucial part of the trust formed between business and customer. If this trust is in question, the relationship is compromised and may cease (e.g., if a private bank loses funds or account information electronically through a publicized security breach, they will probably lose clients as well). 6