Compaq 307560-001 Compaq Enterprise Security Framework - Page 12
Security Market Segments
 |
UPC - 743172470379
View all Compaq 307560-001 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 12 highlights
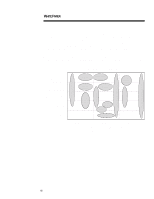
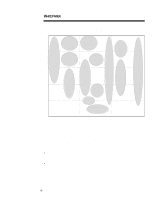
WHITE PAPER (cont.) ... As a result of the diverse threats and vulnerabilities enterprises face, IT managers will need to deploy solutions that serve each security objective on every platform in order to form a complete security solution. For example, if a device does not have robust local authentication measures, parties may use this station as a launching pad for attacks on local network services that trust the identity of individual devices. Similarly, a client that trusts the identity of networked services is vulnerable to attacks from the network. Some solutions, however, can protect different platform levels, depending on how they are implemented. For example, smartcards can act as an identification and authentication solution for a device or as a tool that signs a digital certificate that identifies a user across an external network. Enterprises can use these terms to understand and clarify the purpose and usefulness of various security solutions. A view of the security marketplace using these classifications is shown in Figure 8. - Security Market Segments - Security Objectives Desktop/Server/Laptop Hardware Encryption Software Secure OS, Environments VPN Services Systems Consulting, Security Audit and Testing Identification & Authentication Authorization/ Access Control Privacy Integrity Accountability Tokens Network Hardware Authentication Servers Firewalls Certificate Authorities Encryption Hardware Virus Protection Digital Signature Auditing/ Management Hardware Software Security Products/Technologies Figure 8 Services 12