Compaq 307560-001 Compaq Enterprise Security Framework - Page 11
Certificate Authorities. - file
 |
UPC - 743172470379
View all Compaq 307560-001 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 11 highlights
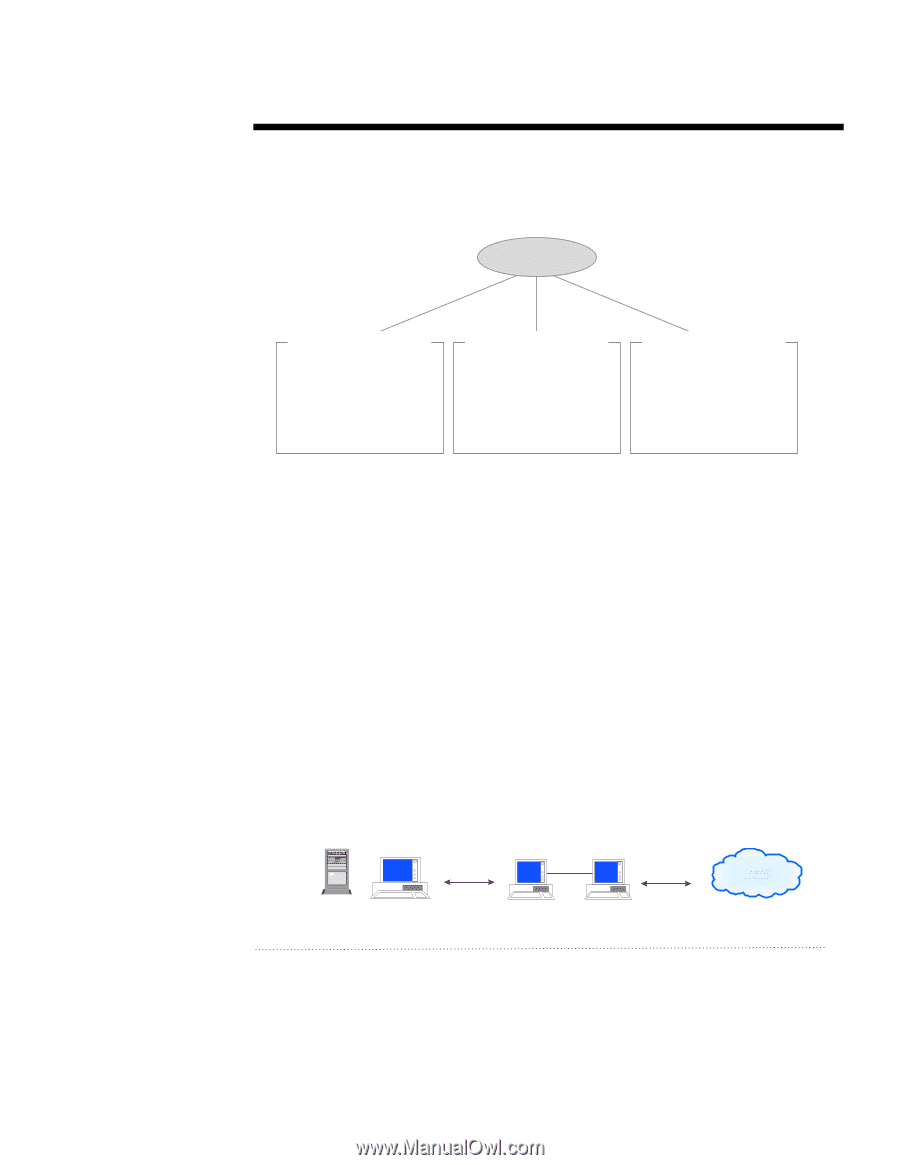
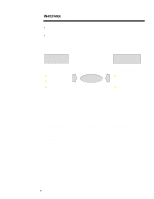
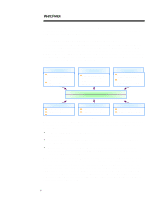
WHITE PAPER (cont.) ... The product and technology categories for security solutions are hardware, software, and services (see figure 6). This initial categorization reveals the variety and complexity of solutions available in the security market. Products/ Technologies Hardware Software Services n Component locks/monitors n BIOS level firmware Ÿ Authentication Ÿ Anti-virus n Encryption chips n Hardware tokens n Network encryption/authentication n Firewalls n Anti-virus n Encryption n Secure OS n Digital signature n Authentication servers n Auditing/Management Tools Figure 6 n Certificate Authorities n Security testing n Systems Integration n Consulting n Network Monitoring n VPN services The hardware category features a variety of implementations, ranging from component locks that physically secure devices through high-speed encryption to chips that improve server performance of cryptographic operations. One of the most significant categories in hardware is portable tokens (including smartcards), which provide a high-performance identification and authentication solution for security environments. Software is the most dynamic category in the security market. Firewalls and anti-virus software are the best understood and furthest developed stand alone solutions on the market, although they are hardly mature product categories. Recently, several notable new software approaches that provide for secure environments have begun to emerge. These approaches range from secure OS and secure APIs to corporate infrastructure software such as certificate servers, single-sign-on solutions, and middleware. In addition, many of the recent innovations in cryptography have been focused on the software category. Security services form an essential part of the security market. In this confusing environment, the expertise of security professionals in consulting and security testing firms is crucial to large enterprises; these services are projected to grow into a $5 billion market by the year 2000. In addition, these companies have crucial ties to the other product categories as installers of solutions (system integrators) or as infrastructure providers (Certificate Authorities). The platform category groups solutions according to the types of attacks they defend against, as well as the types of resources they protect (see Figure 7): Device (Client/Server) Implementation Device solutions protect access to, and the information and resources residing on, devices (e.g., power-onpasswords, physical locks, virus scanning, file encryption). Internal Network Implementation Internal Network solutions protect resources and operations that serve a large number of users within an enterprise over the network (e.g., network log-ins, access control servers, secure messaging, intrusion detecting, network logging software). Figure 7 Public Network External Network Implementation External network solutions protect resources from outside network attack and enable public network operations (e.g., firewalls, certificate servers, VPN software, secure web servers). 11