Compaq 307560-001 Compaq Enterprise Security Framework - Page 20
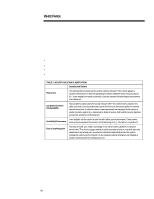
TABLE 4: PLATFORM AND LEVEL-SPECIFIC SOLUTIONS, Level A, Level B, Level C, Client/Server Device,
 |
UPC - 743172470379
View all Compaq 307560-001 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 20 highlights
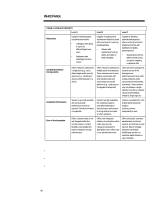
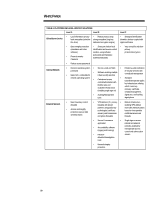
WHITE PAPER (cont.) ... TABLE 4: PLATFORM AND LEVEL-SPECIFIC SOLUTIONS Level A Level B Level C Client/Server Device • Local information privacy- • Robust privacy using basic encryption (selective strong encryption (long key, file, drive). dedicated encryption engine) • Strongest identification: biometric devices coupled with digital certificates • Basic integrity protection (standalone anti-virus software) • Physical security measures • Strong two faction local • Very strong file and drive identification and access control privacy solution, using software protection/encryption (password) and hardware (tokens/smartcards) • Robust access passwords Internal Network • Network operating system • Secure e-mail and Web • Enterprise-wide replication password • Software enabling multiple • Basic ACLs, embedded in robust security services of security services with centralized management network operating system • Centralized access control/authorization with flexible rules and scaleable infrastructure (enabling single sign on) • Standardbased/interoperable public key infrastructure offering which covers key recovery, certificate creation/management, • Auditing/Management tools signatures, and hashing algorhythms External Network • Basic boundary control (firewall) • Access and integrity protection (secure Web server/browser) • VPN abilities (I.D., privacy, • Robust infrastructure integrity) with known enabling VPN abilities partners using public key even with unknown parties technologies (certificate based on interoperable servers) and transmission certificate servers and encryption (firewalls) firewalls • Secure E-commerce application • Accountability software (logging and tracking) • Intrusion detection/investigation tools • Single sign-on across internal and external networks enabled by interoperable access control and authorization servers • Network integrity protection 20