Compaq 307560-001 Compaq Enterprise Security Framework - Page 3
Introduction - 249
 |
UPC - 743172470379
View all Compaq 307560-001 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 3 highlights
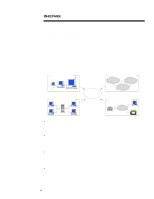
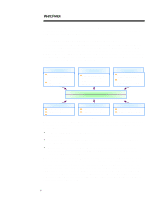
WHITE PAPER (cont.) ... INTRODUCTION Computing security is one of the fastest changing and most complicated areas in the information technology industry today. Each day seems to bring another threat to the security of the world's computing resources. Recently, the Social Security Administration took its operations off line because of privacy fears. In addition, Microsoft has had to re-tool its Explorer browser due to security concerns, and companies have reported a threefold increase in virus incidents over the last year. These items follow the spectacular stories of hackers who broke into and modified the content of the CIA's and Justice Department's web sites, and of computing thief Kevin Mitnick, who gained access to thousands of consumers' credit card numbers. These incidents represent only a subset of the wide variety of threats computer users and administrators must defend against. Making this area even more complex is the confusing array of technologies and solutions, including encryption, firewalls, smartcards, and digital certificates, which are offered to solve these problems. With the overall growth of computing, particularly networked and inter-networked computing, more resources and information are at risk than ever before, with new threats emerging daily. Independent research estimates potential losses from lack of security at between $40-80 billion in the year 2000. Enterprises abilities to protect their resources and capitalize on opportunities will depend on the level of security they enforce. Computing security breaches as well as the concerns of IT managers are rising, yet the deployment of security solutions lags. Over 75% of organizations responding to a recent poll reported a significant computer breach over the last year: the subset of these organizations, which could quantify their losses (249 institutions), reported losses of over $100 million. While most security problems remain basic, such as viruses, password exposure, and physical theft, to date most enterprises have employed only limited or point solutions for security. IT managers must design a practical roadmap to guide their enterprises through this tangle of information, threats, and solutions. In charting a course, they must incorporate the latest technologies, adapt to new threats, and ensure that their solutions do not compromise performance. The Compaq Enterprise Security Framework addresses enterprise security in terms of computing platforms, secure computing technology, and the objectives required of a strong enterprise security policy. The framework also describes solution sets for each platform in terms of "levels" of security. Using the easy-to-understand framework and levels, enterprises can plan a security solution roadmap that meets their business requirements. Compaq's Enterprise Security Framework delivers the critical needs of IT managers and makes the process of securing enterprise computing as easy as possible. 3