Compaq 307560-001 Compaq Enterprise Security Framework - Page 7
Opportunities, Costs/Potential Losses
 |
UPC - 743172470379
View all Compaq 307560-001 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 7 highlights
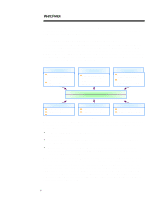
WHITE PAPER (cont.) ... The other potential "unfriendly" force is government. Government regulation of computing security is still evolving; however, it is possible that both the state and federal governments may begin to hold enterprises responsible for the privacy of consumer information. Security Environment: Enterprise Opportunities/Risks The business reasons for deploying enterprise security can be examined from an opportunity/cost perspective. Though these opportunities/costs have not yet been fully explored, and quantifying them is difficult, some estimates have placed potential worldwide enterprise computing losses at $40 billion by the year 2000. In the denominator of the opportunity/cost perspective are the costs of inadequate computing security. In the numerator are both the revenue-enhancing and cost-reducing opportunities enabled by sound computing security. E-Commerce n Opportunity to sell existing goods over web n Opportunity to enter new business areas Consumer Intimacy n Opportunity to create better relationships with consumers over the web Partner Efficiencies n Opportunity to share supply chain data n Opportunity to implement affordable EDI Opportunities Costs/Potential Losses Information Privacy n Revenue/Value n Competitive Position n Reduced Confidence Application Availability n Operation Downtime n Repair/Recovery Costs Figure 4 Asset vulnerability n Physical (computers) n Digital (software, funds) The first risk category (see Figure 4) in the denominator is the potential loss of information privacy. When sensitive information is compromised and falls into unfriendly hands, enterprises can face several types of losses: • They can lose revenue/value when merger and acquisition plans or contract bid information is compromised. • They can also lose their competitive position when product plans or designs are stolen or pricing strategies are spread to a competitor. • Additionally, there is the reduced confidence in a company that results from a breach of security such as the early release of an SEC report, the compromising of medical records, or the theft of employee HR information. Another area of risk well known to IT managers is application availability. A virus or other attack can create significant costs for an enterprise in the areas of operational downtime and repair or recovery. The final area of potential loss is the actual assets under enterprise control. Obviously, there are the losses associated with the value of the hardware (RSA reports that 200,000 laptops were stolen in 1996), but many businesses must also vigorously protect their digital assets. The entire business model of companies whose products largely reside in the digital domain (software companies, banks, etc.) is dependent upon the security of their assets; they must deploy the most advanced measures to protect them. 7