Dell PowerEdge M420 Dell PowerConnect M8024-k Release Notes - Page 10
Switch Auditing, Authentication
 |
View all Dell PowerEdge M420 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 10 highlights
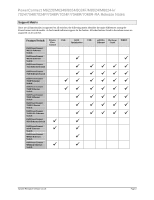
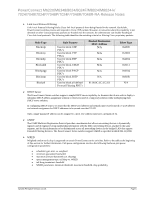
Switch Auditing Switch auditing enhances network security by logging sensitive administrative actions. Switch auditing logs the following actions: Successful login Unsuccessful attempt to login Logout out from the switch Timed out logout from the switch Download file to the switch Upload file from the switch Remove file from the flash File changes on the flash Clear configuration Add or remove user Change user access level Use of a SYSLOG server for monitoring network events is highly recommended. Authentication The PowerConnect switches support authentication via a number of methods. The methods are specified in named lists. Lists may be assigned to the enable and login access methods. The supported authentication methods are: Enable Line RADIUS TACACS IAS Local None Methods are attempted in the order specified in the authentication list. If the authentication method rejects authentication, the user login is rejected. If an authentication method fails, e.g. unable to contact the authentication server, the next method in the list is attempted. Only the RADIUS and TACACS methods can fail and therefore should be specified first in an authentication list. The other methods will never fail and therefore should be specified after RADIUS or TACACS in a list. The 802.1x authentication list cannot be named and only supports the RADIUS, IAS, or none authentication methods. 802.1x authentication supports a single authentication method, not a list of methods. 8 System Firmware Version 4.1.0.6