Dell PowerEdge M420 Dell PowerConnect M8024-k Release Notes - Page 9
Management IP Address Conflict Detection, Email Alerting, 1x Monitor Mode, Time Controlled ACLs,
 |
View all Dell PowerEdge M420 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 9 highlights
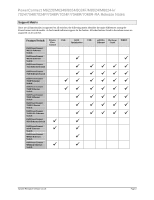
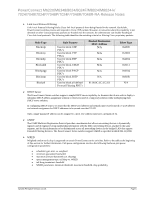
PowerConnect M6220/M6348/8024/8024F/M8024/M8024-k/ 7024/7048/7024P/7048P/7024F/7048R/7048R-RA Release Notes Management IP Address Conflict Detection Management IP address conflict detection actively looks for duplicate IP address assignment and logs conflicts. Only the last identified IPv4 address conflict is retained for display by a show command. Administrators may examine the in- memory logs or the output from a SYSLOG server to identify the historical IP address conflicts. If console logging is enabled for traps, a message will appear on the console indicating that an address conflict has occurred. Email Alerting Email alerting allows administrators to be notified regarding system events. Multiple email addresses can be configured. The system will attempt to resolve mail servers specified with a DNS FQDN immediately and, if successful, store the mail-server as an IP address. If a new IP address is subsequently assigned to the mail server, the operator will need to re-assign the email address on the switch. Only the Mail User Agent functionality of RFC 4409 is implemented. The PowerConnect switch does not implement SMTP server functionality. 802.1x Monitor Mode Monitor mode is a special debug mode that assists network administrators in configuring new authentication servers. Users attempting to authenticate using the authentication server are always granted access when monitor mode is enabled. All interactions with the supplicant and the authentication server are logged. Administrators are cautioned against enabling monitor mode in a deployed network where 802.1x users may gain access to sensitive network resources. Time Controlled ACLs Time controlled ACLs allow administrators to apply ACLs based on the time of day. Both periodic and absolute time periods may be configured. Administrators are cautioned that invalid (overlapping) periodic entries within a time range will cause the time range to not be applied. Administrators are advised to test their periodic entries and validate that they become active as expected before deploying the time ranges in a production network. Administrators can check if a time range is active by using the show time-range command. It is recommended to enable ACL logging to ensure notice of ACL activation and de-activation. SNTP over IPv6 SNTP operates over IPv4 and IPv6 and may be configured using IPv4 or IPv6 addresses or DNS. Strong Passwords The strong passwords feature allows administrators to specify that switch administrator passwords meet certain characteristics considered to enhance network security. Administrators are advised that the minimum character classes configuration must be enabled (value equal to 1 or greater) along with enabling the strong password feature before the other minimum character class configurations are enforced. These character class configuration are: Minimum number of uppercase letters. Minimum number of lowercase letters. Minimum number of numeric characters. Minimum number of special characters The password strength restrictions do not apply to users configured for the internal authentication server. System Firmware Version 4.1.0.6 Page 7