TP-Link TL-WN7200ND User Guide - Page 21
TL-WN7200N, PBC Method, II. PIN Method, QSS- QSS BUTTON mode
 |
UPC - 845973050535
View all TP-Link TL-WN7200ND manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 21 highlights
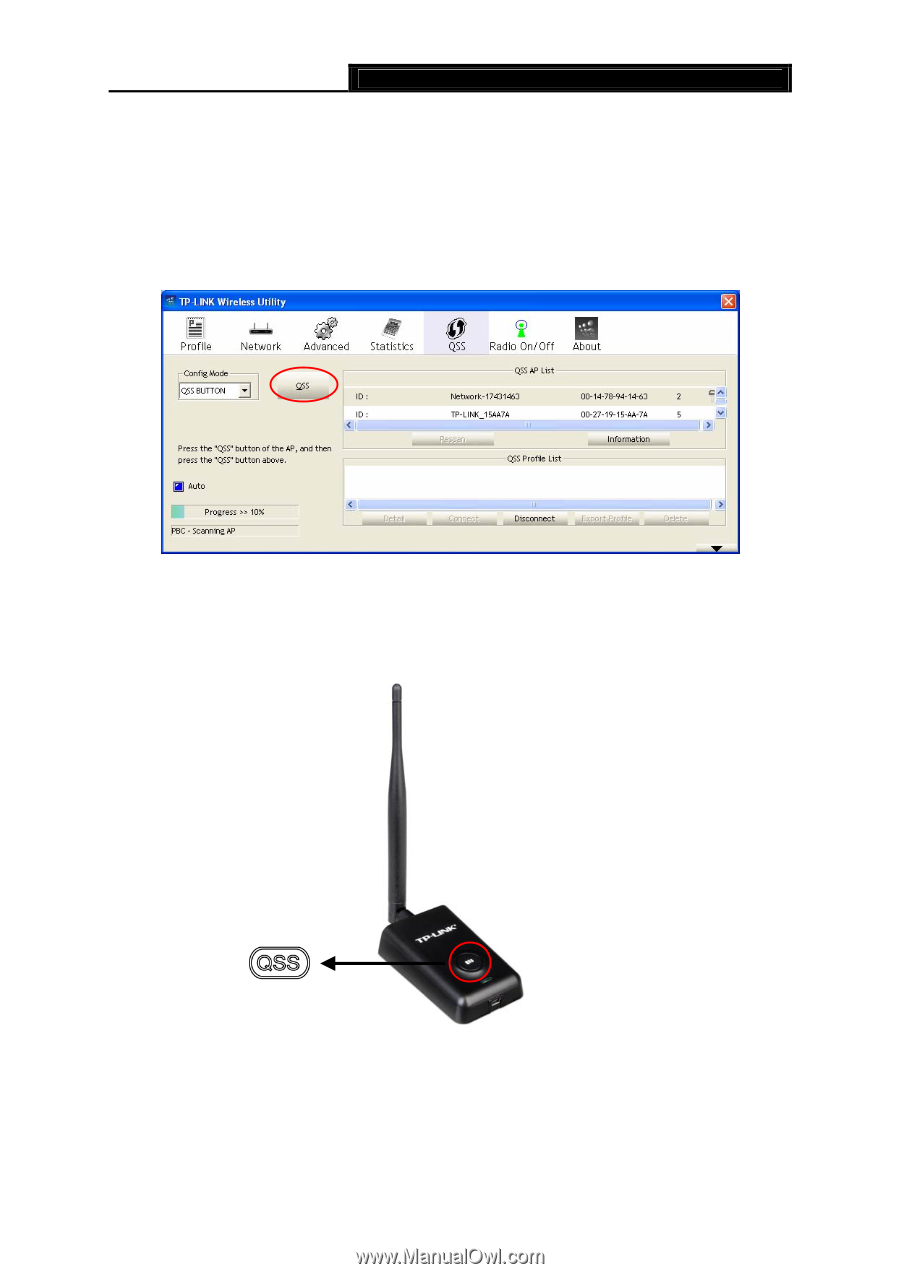
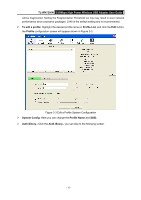
TL-WN7200N 150Mbps High Power Wireless USB Adapter User Guide ) Note: To build a successful connection by QSS, you should also do the corresponding configuration of the Access Point for QSS or WPS function meanwhile. I. PBC Method If your Access Point is equipped with a push-button for Wi-Fi Protected Setup, you can connect the adapter to the Access Point by Push QSS Button method. Figure 3-9 QSS- QSS BUTTON mode Step 1 Click the QSS button (marked by the red circle) on the screen as Figure 3-9. Or: Press and hold the QSS button on the adapter (shown on the following figure) for 2 or 3 seconds. Step 2 Press the QSS button on your Access Point device to build the connection. II. PIN Method If your Access Point supports Wi-Fi Protected Setup and the PIN method, you can add the adapter to the network by the following two ways: - 16 -