ZyXEL G-200 User Guide - Page 45
Appendix B, Wireless LAN With IEEE 802.1x, Security Flaws with IEEE 802.11
 |
View all ZyXEL G-200 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 45 highlights
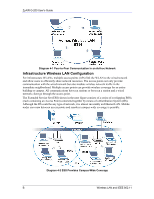
ZyAIR G-200 User's Guide Appendix B Wireless LAN With IEEE 802.1x As wireless networks become popular for both portable computing and corporate networks, security is now a priority. Security Flaws with IEEE 802.11 Wireless networks based on the original IEEE 802.11 have a poor reputation for safety. The IEEE 802.11b wireless access standard, first published in 1999, was based on the MAC address. As the MAC address is sent across the wireless link in clear text, it is easy to spoof and fake. Even the WEP (Wire Equivalent Privacy) data encryption is unreliable as it can be easily decrypted with current computer speed Deployment Issues with IEEE 802.11 User account management has become a network administrator's nightmare in a corporate environment, as the IEEE 802.11b standard does not provide any central user account management. User access control is done through manual modification of the MAC address table on the access point. Although WEP data encryption offers a form of data security, you have to reset the WEP key on the clients each time you change your WEP key on the access point. IEEE 802.1x In June 2001, the IEEE 802.1x standard was designed to extend the features of IEEE 802.11 to support extended authentication as well as providing additional accounting and control features. It is supported by Windows XP and a number of network devices. Advantages of the IEEE 802.1x ♦ User based identification that allows for roaming. ♦ Support for RADIUS (Remote Authentication Dial In User Service, RFC 2138, 2139) for centralized user profile and accounting management on a network RADIUS server. ♦ Support for EAP (Extensible Authentication Protocol, RFC 2486) that allows additional authentication methods to be deployed with no changes to the access point or the wireless stations. RADIUS Server Authentication Sequence The following figure depicts a typical wireless network with a remote RADIUS server for user authentication using EAPOL (EAP Over LAN). Wireless LAN With IEEE 802.1x C