D-Link DGS-6600-48T Configuration Guide - Page 465
DHCP Operation concept, DHCP Snooping Configuration Commands, Enabling and Disabling DHCP Snooping
 |
View all D-Link DGS-6600-48T manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 465 highlights
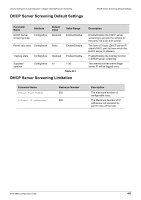
Volume 8-Security & Authentication / Chapter 44-DHCP Snooping Configuration DHCP Snooping Configuration Commands the source MAC address and the DHCP client hardware address. If the addresses match (default), the switch forwards the packet. Otherwise the switch drops the packet. The switch validates DHCP packets received on the untrusted interfaces of VLANs with DHCP snooping enabled. DHCP Operation concept Because the packets for obtaining IP addresses through DHCP are in the form of broadcast, some illegal servers may prevent users from obtaining IP addresses, or even cheat and steal user information. To solve this problem, DHCP Snooping classifies the ports into two types: TRUST port and UNTRUST port. The device forwards only the DHCP reply packets received through the TRUST port while discarding all the DHCP reply packets from the UNTRUST port. In this way, the illegal DHCP Server can be shielded by setting the port connected to the legal DHCP Server as a TRUST port and other ports as UNTRUST ports. DHCP Snooping binding database: By snooping the packets between the DHCP Clients and the DHCP Server, DHCP Snooping combines the IP address, MAC address, VID, port and lease time into an entry to form a DHCP Snooping user database. DHCP Snooping Configuration Commands Enabling and Disabling DHCP Snooping The DHCP snooping function snoops the DHCP packets arriving at the un-trusted interface on VLAN that is enabled for DHCP snooping. With this function, the DHCP packets come from the untrusted interface can be validated, and a DHCP binding database will be constructed for the DHCP snooping enabled VLAN. The binding database provides IP and MAC binding information that can be further used by the IP source guard and dynamic ARP inspection process. Use the ip dhcp snooping command to globally enable DHCP snooping and use the ip dhcp snooping vlan command to enable DHCP snooping for a VLAN. DHCP snooping process occurs during the relay agent relays the packet. To enable the DHCP relay service, relay agent service must be enabled by service dhcp command, and the server address to relay the packet must be configured by the ip helper address. Command ip dhcp snooping no ip dhcp snooping Explanation Use this command to globally enable DHCP snooping. Use no command to disable DHCP snooping. These examples shows how to enable and disable DHCP snooping: DGS-6600:15# configure terminal DGS-6600:15(config)# ip dhcp snooping DGS-6600:15(config DGS-6600:15# configure terminal DGS-6000:15(config)# no ip dhcp snooping DGS-6600:15(config)# DGS-6600 Configuration Guide 465