Lexmark X782e PKI-Enabled Pre-Installation Guide - Page 31
All Users Can Use This Fileshare - no restrictions
 |
View all Lexmark X782e manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 31 highlights
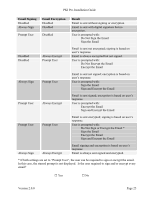
PKI Pre-Installation Guide 1. Fileshare Authorization. Each fileshare can have its own user authorization. This is only available if User Authorization is enabled in PKI/AD Authentication application. If the user is not authorized, this fileshare is not displayed for the user to select. Select the user authorization for this fileshare. □ All Users Can Use This Fileshare - no restrictions □ Only Users in the Groups specified in item 2 can use this fileshare □ All Users Except those in the Groups specified in item 2 can use this fileshare 2. If User Authorization is enabled and the file shareaccess setting in item 1 requires groups to be included or excluded, list the Active Directory group names here. 3. Display Name. If the user has access to more than one fileshare, all the possible choices are displayed in a list. What name should be given to the fileshare? File Share Display Name 4. UNC Path. Each fileshare needs the UNC Path that corresponds to it. If looking up data from LDAP to create the UNC Path, use a "%u" (no quotes) in the path to represent the data. The "%u" will be replaced after the LDAP lookup by the actual data to create the actual UNC path. UNC Path 5. Replacement Value. If a "%u" was specified in the UNC Path (item 4), the value that replaces the "%u" must be selected. The value replacing "%u" is: □ User Principal Name □ Email Address □ EDI-PI □ LDAP Lookup using LDAP Configuration: □ LDAP - Default Configuration (as specified in section 2.5) □ LDAP - Configuration 1 (as specified in section 8.1) □ LDAP - Configuration 2 (as specified in section 8.2) □ LDAP - Configuration 3 (as specified in section 8.3 LDAP Attribute Version 2.0.0 Page 27