HP D330 HP Business Desktop BIOS - Page 10
Removable Media Boot enable/disable - motherboard
 |
View all HP D330 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 10 highlights
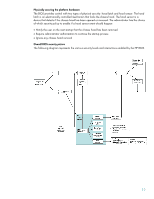
Administrator authentication also protects BIOS flash upgrades. If the setup password is set, the BIOS cannot be upgraded without providing that setup password or an administrator smart card. This helps the administrator maintain a common BIOS image and prevent undesired upgrades. All other BIOS configuration settings, including security policies, are also protected by administrator authentication. This includes all settings in F10 setup, except the time and date. The time and date is the only function that is allowed to be changed without administrator privileges. By default, all BIOS settings are protected by administrator authentication even while the OS is running. As a security policy option, the administrator can set the BIOS to allow the OS to change legacy resources even when administrator authentication is enabled. Securing the BIOS flash The computer BIOS image is stored in a nonvolatile memory device on the motherboard known as flash memory. In order for the computer to start and run correctly, this flash memory must contain a valid BIOS image. The image in the flash memory may be reprogrammed from time to time to update the BIOS version. Virus software, such as the Chernobyl virus, has been able to corrupt nonvolatile memory, including flash memory, on some computers. When this happens, the computer motherboard may have to be replaced because the computer may not be able to restart. The HP BIOS uses hardware mechanisms on most HP Business Desktops to prevent access to the BIOS flash memory by any software other than the BIOS. This hardware traps any attempts to update the flash memory that do not originate from the BIOS itself. BIOS images that work with HP Windows-based BIOS update tools (flash tools), such as HPQFlash and SSM, contain a digital signature that allows the flash tools to authenticate the BIOS image. This ensures that the image originated from HP and has not been corrupted or tampered with in any way. As mentioned earlier, administrator authorization allows the system administrator to control all BIOS image updates. Securing startup The power-on password or user smart card functions as a user authentication and boot access control mechanism. If this password is set or smart card established, the user will be prompted to enter this password or smart card on each startup, and optionally on each restart. The startup process is halted if the correct password or smart card is not entered. Device boot control is a series of settings that control which devices can be booted and in what order. This feature is important to prevent subversion of the installed OS as described earlier. The settings in this category are 1. Network Service Boot (enable/disable) 2. Removable Media Boot (enable/disable) 3. Remote Wake Boot Source (controls which device will boot on wakeup) 4. Boot Order (controls which devices can be booted and in what order) 5. USB port and mass storage controller disable (mentioned earlier) 6. DriveLock Securing portable data Computers that contain mobile technology hard disk drives used in MultiBay slots can protect the data on those drives with a DriveLock password. The password is stored on the drive and the drive firmware controls access so that the DriveLock security goes with the drive, not the platform. Each time the computer is restarted, the drive will remain inaccessible until the DriveLock password is provided. This drive locking mechanism is an industry standard (ATA-5). It is recommended that the system administrator establish a master DriveLock password on each drive and then allow the user to establish the user DriveLock password. This is the only way to recover a drive if the DriveLock password is lost. The master DriveLock password provides a mechanism to clear 10