HP D330 HP Business Desktop BIOS - Page 9
Preboot security is vital to OS security, User authentication, Securing the Trusted Platform State - bios update
 |
View all HP D330 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 9 highlights
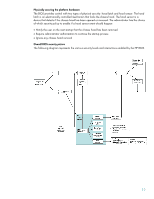
Preboot security is vital to OS security Since the computer BIOS is the first operation to run at startup (pre-OS boot or preboot) and ultimately controls which operating system software is loaded, BIOS preboot security is a vital link in total computer security. Without BIOS preboot security, it is not difficult to subvert the security of the installed operating system by booting to a different OS on removable media (such as CD, diskette, USB key, etc). When a rogue OS is started on removable media, instead of the installed OS, the security policies of the installed OS are not in force. This gives an unauthorized user (hacker) the ability to examine and potentially compromise any data or stored security policies of the computer. Tools such as ERD Commander exist just for the purpose of bypassing OS security and manipulating OS security settings. Installing a power-on password might be sufficient for the user to trust that no one else has accessed their computer. However, to satisfy the system administrator that not even the owner of the power-on password can boot from removable media, the system administrator can use the BIOS preboot security features to select which devices are bootable. This can effectively prevent undesirable OS loads from removable media (such as diskette or USB external devices). In addition, computer I/O ports can also be locked down and hidden. In the hidden state, no program has access to these ports, not even the operating system. This can help prevent unauthorized removal of sensitive data. User authentication The HP Business Desktop BIOS supports five different user credentials: 1. Setup password-sometimes called the administrator password, controls updates to BIOS options (F10 setup) and BIOS configuration and can be used in place of the power-on password to boot the computer (administrator authentication) 2. Power-on password-controls booting into the Operating System (user authentication) 3. Two-Level DriveLock password-controls access to HDD contents using industry-standard ATA security features on supported drives installed in MultiBay slots. This password may be set to match the power-on password, in which case the BIOS will automatically unlock the HDD using the power-on password typed by the user. NOTE: for desktops, DriveLock is supported on Multibay only, not standard hard drives. 4. User Smart Card-Takes place of power-on password when enabled 5. Administrator Smart Card-takes the place of the setup password Securing the Trusted Platform State (TPS) Administrator authentication is enabled by setting a setup password or by creating an administrator smart card. Administrator authentication provides controls over important BIOS functions and security policies. HP recommends that a company's IT department establish administrator authentication on all machines to control all changes to the BIOS. The IT department can establish a common, organization-wide setup password or administrator smart card credential to provide easy access to all machines by system administrators. If no setup password or administrator smart card is established, then administrator authentication is disabled, and anyone or any program can change BIOS settings and anyone can make BIOS flash upgrades. A few security policy settings, however, cannot be enabled without first enabling administrator authentication. The first feature of administrator authentication is that it can override user authentication (see below). This allows administrators access to a machine even if the user has a power-on password set and the user forgets the password, or does not have the user smart card, or the administrator needs access to the machine in the user's absence. The setup password can be entered at the password prompt in place of the power-on password, or the administrator smart card can be inserted at the smart card prompt in place of the user smart card. 9