Ricoh Aficio MP 2851 Security Target - Page 34
Security Requirements
 |
View all Ricoh Aficio MP 2851 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 34 highlights
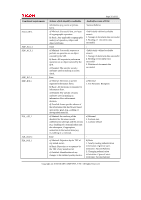
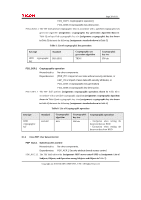
Page 34 of 81 6 Security Requirements This section describes the security functional requirements, security assurance requirements, and security requirements rationale. 6.1 Security Functional Requirements This section describes the TOE security functional requirements for fulfilling the security objectives defined in "4.1 Security Objectives for TOE". The security functional requirements are quoted from the requirement defined in the CC Part2. The part with assignment and selection defined in the CC Part2 are identified with [bold face and brackets]. 6.1.1 Class FAU: Security audit FAU_GEN.1 Audit data generation Hierarchical to: No other components. Dependencies: FPT_STM.1 Reliable time stamps. FAU_GEN.1.1 The TSF shall be able to generate an audit record of the following auditable events: a) Start-up and shutdown of the Audit Functions; b) All auditable events for the [selection: not specified] level of audit; and c) [assignment: auditable events of the TOE shown in Table 4]. Table 4 shows the actions (CC rules) recommended by the CC as auditable for each functional requirement and the corresponding auditable events of the TOE. Table 4: List of auditable events Functional requirements Actions which should be auditable Auditable events of TOE FAU_GEN.1 FAU_SAR.1 FAU_SAR.2 FAU_STG.1 FAU_STG.4 FCS_CKM.1 None a) Basic: Reading of information from the audit records. a) Basic: Unsuccessful attempts to read information from the audit records. None a) Basic: Actions taken due to the audit storage failure. a) Minimal: Success and failure of the activity. b) Basic: The object attribute(s), and object value(s) excluding any sensitive Auditable events not recorded. Auditable events not recorded. Auditable events not recorded. 1. HDD cryptographic key generation (Outcome: Copyright (c) 2010 RICOH COMPANY, LTD. All Rights Reserved.