Ricoh Aficio MP 2851 Security Target - Page 42
FIA_AFL.1, Authentication failure handling
 |
View all Ricoh Aficio MP 2851 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 42 highlights
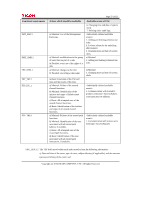
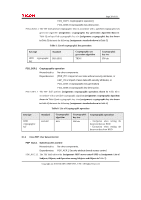
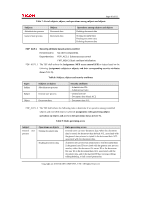
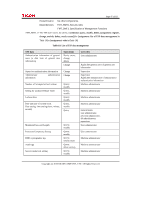
Page 42 of 81 following types of subject and information security attributes: [assignment: subjects or information and their corresponding security attributes shown inTable 12]. Table 12: Security attributes corresponding to subjects or information Type Subjects or information Security attributes Subject Fax process on Fax Unit No security attributes Subject Fax reception process on Controller Board No security attributes Information Data received from a telephone line Data type (Note: "Data type" means the type of data received from a telephone line and indicates whether this is fax or non-fax data.) FDP_IFF.1.2 The TSF shall permit an information flow between a controlled subject and controlled information via a controlled operation if the following rules hold: [assignment: after the type of received data from a telephone line is recognised as fax data, the fax process on the Fax Unit allows Fax Reception on the Controller Board to let data received from a telephone line pass]. FDP_IFF.1.3 The TSF shall enforce the [assignment: no additional information flow control SFP rules]. FDP_IFF.1.4 The TSF shall explicitly authorise an information flow based on the following rules: [assignment: no rules, based on security attributes that explicitlyauthorise information flows]. FDP_IFF.1.5 The TSF shall explicitly deny an information flow based on the following rules: [assignment: no rules, based on security attributes that explicitly deny information flows]. 6.1.4 Class FIA: Identification and authentication FIA_AFL.1 Authentication failure handling Hierarchical to: No other components. Dependencies: FIA_UAU.1 Timing of authentication. FIA_AFL.1.1 TSF shall detect when [selection: an administrator (refinement: the machine administrator) configurable positive integer within [assignment: 1 to 5]] unsuccessful authentication attempts occur related to [assignment: the consecutive numbers of times of authentication failure for each user in the authentication events shown in Table 13]. Table 13: List of authentication events Authentication events User authentication using the control panel Copyright (c) 2010 RICOH COMPANY, LTD. All Rights Reserved.