Ricoh Aficio MP 2851 Security Target - Page 61
Rationale for Removing Dependencies on FCS_CKM.4
 |
View all Ricoh Aficio MP 2851 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 61 highlights
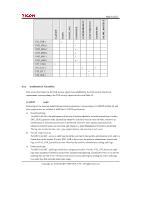
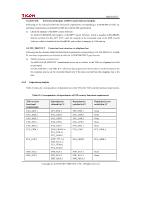
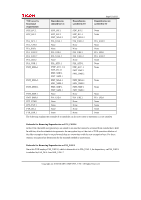
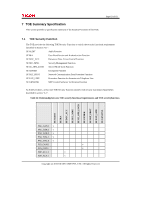
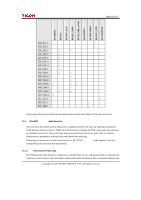
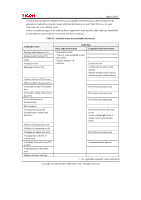
Page 61 of 81 TOE security functional requirements FDP_IFC.1 FDP_IFF.1 FIA_AFL.1 FIA_ATD.1 FIA_SOS.1 FIA_UAU.2 FIA_UAU.7 FIA_UID.2 FIA_USB.1 FMT_MSA.1 FMT_MSA.3 FMT_MTD.1 FMT_SMF.1 FMT_SMR.1 FPT_STM.1 FPT_TST.1 FTP_ITC.1 FTP_TRP.1 Dependencies claimed by CC FDP_IFF.1 FDP_IFC.1 FMT_MSA.3 FIA_UAU.1 None None FIA_UID.1 FIA_UAU.1 None FIA_ATD.1 [FDP_ACC.1 or FDP_IFC.1] FMT_SMF.1 FMT_SMR.1 FMT_MSA.1 FMT_SMR.1 FMT_SMF.1 FMT_SMR.1 None FIA_UID.1 None None None None Dependencies satisfied in ST FDP_IFF.1 FDP_IFC.1 FMT_MSA.3 FIA_UAU.2 None None FIA_UID.2 FIA_UAU.2 None FIA_ATD.1 FDP_ACC.1 FMT_SMF.1 FMT_SMR.1 FMT_MSA.1 FMT_SMR.1 FMT_SMF.1 FMT_SMR.1 None FIA_UID.2 None None None None Dependencies not satisfied in ST None None FIA_UAU.1 None None FIA_UID.1 FIA_UAU.1 None None None None None None FIA_UID.1 None None None None The following explains the rationale of acceptability in all cases where a dependency is not satisfied: Rationale for Removing Dependencies on FCS_CKM.4 In this TOE, the HDD encryption keys are stored in an area that cannot be accessed from outside the Ic Hdd. In addition, after the administrator generates the encryption keys at the start of TOE operation,deletion of the older encryption keys is not performed: they are overwritten with the new encryption keys. For these reasons, encryption key destruction by the standard method is unnecessary. Rationale for Removing Dependencies on FIA_UAU.1 Since this TOE employs FIA_UAU.2, which is hierarchical to FIA_UAU.1, the dependency on FIA_UAU.1 is satisfied by FIA_AFL.1 and FIA_UAU.7. Copyright (c) 2010 RICOH COMPANY, LTD. All Rights Reserved.