Ricoh Aficio MP 2851 Security Target - Page 55
Security Requirements Rationale
 |
View all Ricoh Aficio MP 2851 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 55 highlights
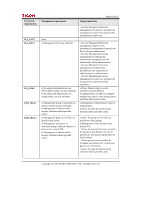
Page 55 of 81 6.3 Security Requirements Rationale This section describes the rationale behind the security requirements. If all security functional requirements are satisfied as below, the security objectives defined in "4.1Security Objectives for TOE" are fulfilled. 6.3.1 Tracing Table 22 shows the relationship between the TOE security functional requirements and TOE security objectives. The "v" in the table indicates that the TOE security functional requirement fulfills the TOE security objective. Table 22 shows that each TOE security functional requirementfulfills at least one TOE security objective. Table 22: Relationship between security objectives and functional requirements O.AUDIT O.I&A O.DOC_ACC O.MANAGE O.MEM.PROTECT O.NET.PROTECT O.GENUINE O.LINE_PROTECT FAU_GEN.1 v FAU_SAR.1 v FAU_SAR.2 v FAU_STG.1 v FAU_STG.4 v FCS_CKM.1 v FCS_COP.1 v FDP_ACC.1 v FDP_ACF.1 v FDP_IFC.1 v FDP_IFF.1 v FIA_AFL.1 v FIA_ATD.1 v FIA_SOS.1 v FIA_UAU.2 v FIA_UAU.7 v FIA_UID.2 v Copyright (c) 2010 RICOH COMPANY, LTD. All Rights Reserved.