TRENDnet TEW-MP1U User's Guide - Page 19
Wireless Security - WPA2-PSK
 |
UPC - 710931600322
View all TRENDnet TEW-MP1U manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 19 highlights
Wireless Security - WPA2-PSK If "WPA2-PSK" is selected, the screen will look like the following example. Security System Passphrase Encryption Figure 15: WPA2-PSK Screen WPA2-PSK This is a further development of WPA-PSK, and offers even greater security. Enter the Keyword key value. Data is encrypted using a key derived from the PSK. Other Wireless Stations must use the same PSK. The PSK must be from 8 to 63 characters in length. Select the desired option. Other Wireless Stations must use the same method. Page 17
Page 17
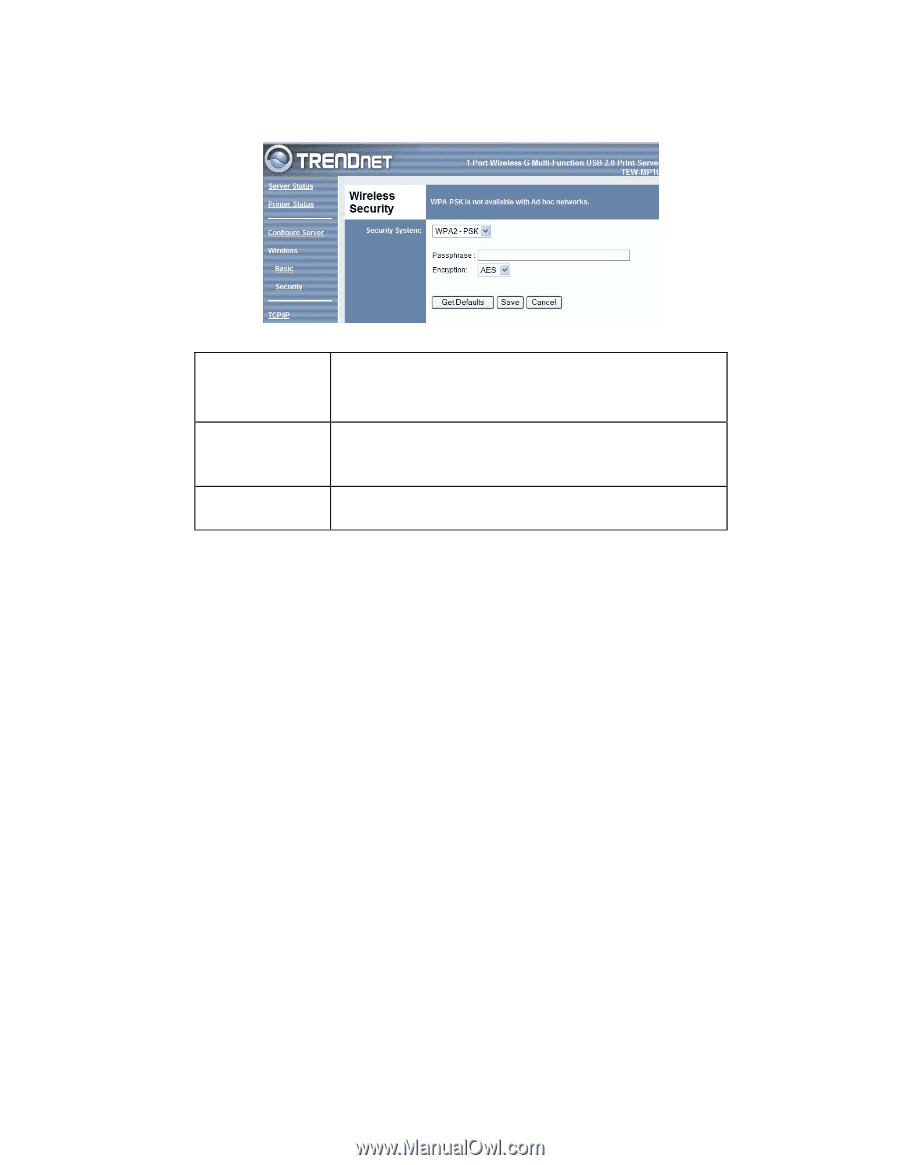
Wireless Security - WPA2-PSK
If "WPA2-PSK" is selected, the screen will look like the following example.
Figure 15: WPA2-PSK Screen
Security
System
WPA2-PSK
This is a further development of WPA-PSK, and offers even
greater security.
Passphrase
Enter the Keyword key value. Data is encrypted using a key
derived from the PSK. Other Wireless Stations must use the
same PSK. The PSK must be from 8 to 63 characters in length.
Encryption
Select the desired option. Other Wireless Stations must use the
same method.