ZyXEL G-300 User Guide - Page 21
Wireless LAN Security, RTS Threshold, Profile Security Settings
 |
View all ZyXEL G-300 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 21 highlights
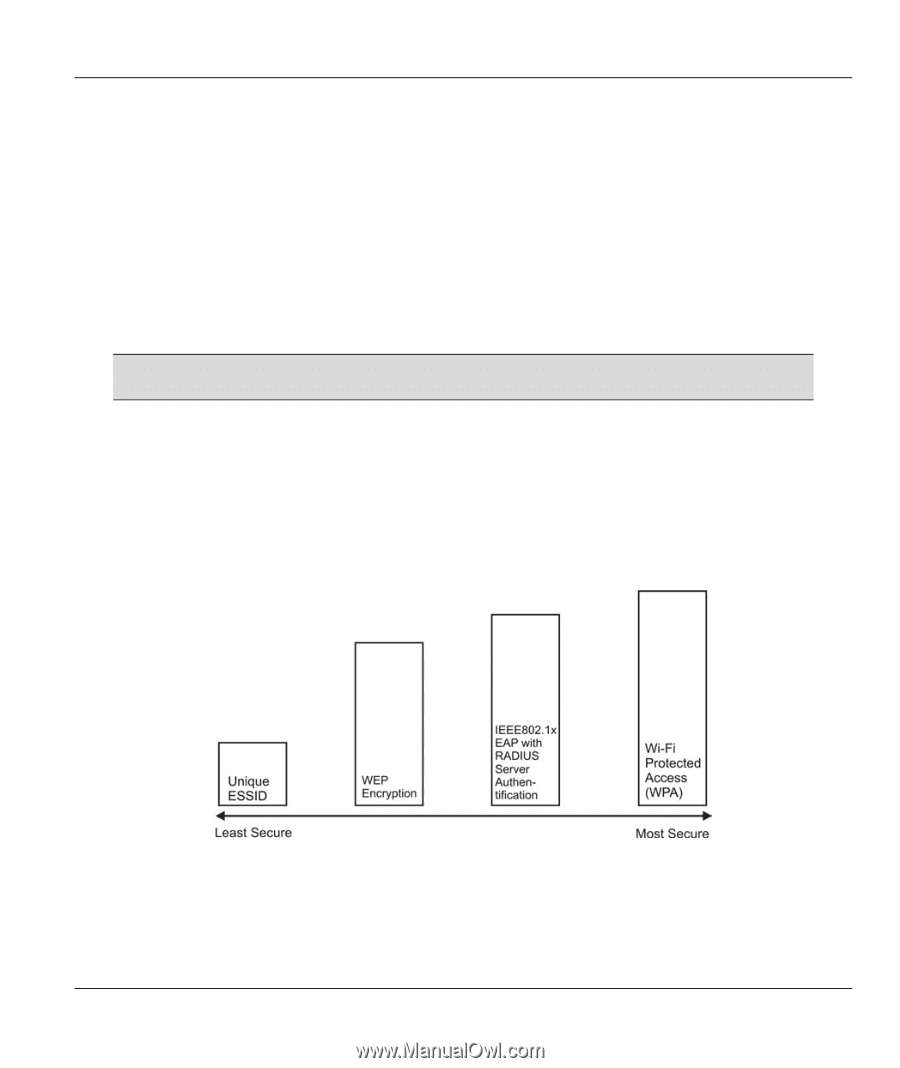
ZyAIR G-300 User's Guide send it. The AP then responds with a CTS (Clear to Send) message to all other stations within its range to notify them to defer their transmission. It also reserves and confirms with the requesting station the time frame for the requested transmission. Stations can send frames smaller than the specified RTS Threshold directly to the AP without the RTS (Request To Send)/CTS (Clear to Send) handshake. You should only configure RTS Threshold if the possibility of hidden nodes exists on your network and the "cost" of resending large frames is more than the extra network overhead involved in the RTS (Request To Send)/CTS (Clear to Send) handshake. If the RTS Threshold value is greater than the Frag Threshold value, then the RTS (Request To Send)/CTS (Clear to Send) handshake will never occur as data frames will be fragmented before they reach RTS Threshold size. Enabling the RTS threshold causes redundant network overhead that may affect throughput performance. 2.2 Wireless LAN Security Wireless LAN security is vital to your network to protect wireless communication between wireless stations and the wired network. The figure below shows the possible wireless security levels on your ZyAIR. EAP (Extensible Authentication Protocol) is used for authentication and utilizes dynamic WEP key exchange. It requires interaction with a RADIUS (Remote Authentication Dial-In User Service) server either on the WAN or your LAN to provide authentication service for wireless stations. Figure 2-6 Wireless LAN Security Levels Configure the wireless LAN security using the Profile Security Settings screen. If you do not enable any wireless security on your ZyAIR, the ZyAIR's wireless communications are accessible to any wireless networking device that is in the coverage area. Using the ZyAIR Utility 2-5