ZyAIR G-300 User’s Guide
DD
Index
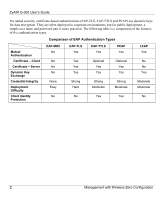
IEEE 802.1X
..........................................
2-15
IEEE 802.1X authentication
...................
2-15
Independent Basic Service Set
......
See
IBSS
Information for Canadian Users
..................
iv
Caution
....................................................
iv
Note
.........................................................
iv
Infrastructure
............................................
2-2
L
Link quality
.............................................
2-11
Link strength
..........................................
2-12
M
MD5
............................................................
Y
Message Digest Algorithm 5
..........
See
MD5
Message Integrity Check
.........................
2-7
MIC
................
See
Message Integrity Check
N
Network driver version
...........................
2-21
Network Type
...........................................
2-1
Ad-Hoc(IBSS)
.......................................
2-1
Infrastructure
........................................
2-2
NIC firmware version
.............................
2-21
Nitro Time
..............................................
2-13
O
Online Registration
.....................................
iii
Open authentication mode
.......................
2-6
Operating Mode
...............
See
Network Type
P
PEAP
..........................................................
Y
power save
.............................................
2-12
Preface
......................................................
xiii
Pre-Shared Key (PSK)
...........................
2-15
problem description
.................................
4-1
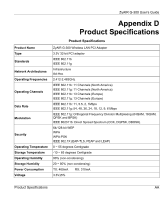
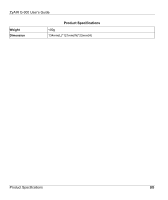
Product specifications
..............................
AA
profile
.....................................................
2-10
Protected EAP
..............................
See
PEAP
R
radio frequency
........................................
2-1
Related Documentation
............................
xiii
Roaming
...................................................
2-3
Example
................................................
2-3
RTS (Request To Send)
...................
2-4, 2-5
RTS Threshold
................................
2-4, 2-13
RTS/CTS handshake
...............................
2-5
S
Security screen, the
...............................
2-13
Service Set Identity
.......................
See
SSID
Shared authentication mode
....................
2-6
Site Survey
....................................
2-18, 2-19
SSID
.......................................
2-1, 2-11, 2-19
State
.......................................................
2-11
Syntax Conventions
..................................
xiii
T
Temporal Key Integrity Protocol
...............
2-7
Threshold
...............................................
2-13
Throughput
.............................................
2-11
TKIP
....
See
Temporal Key Integrity Protocol
TLS
..............................................................
Y
Transmission rate
.....................................
2-1
Transmission rates
.................................
2-11
Transmission speeds
.............................
2-11
Transport Layer Security
.................
See TLS
Troubleshooting
.......................................
4-1
Checking Hardware Conflict
.................
4-1
Communication problems
.....................
4-1
Radio interference
................................
4-2
Starting ZyAIR Utility
............................
4-1
TTLS
...........................................................
Y
Tunneled Transport Layer Service
See
TTLS