ZyXEL NSA-2401 User Guide - Page 258
Product Specifications, NSA-2401 User's Guide, Firmware Features continued, Change Password
 |
View all ZyXEL NSA-2401 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 258 highlights
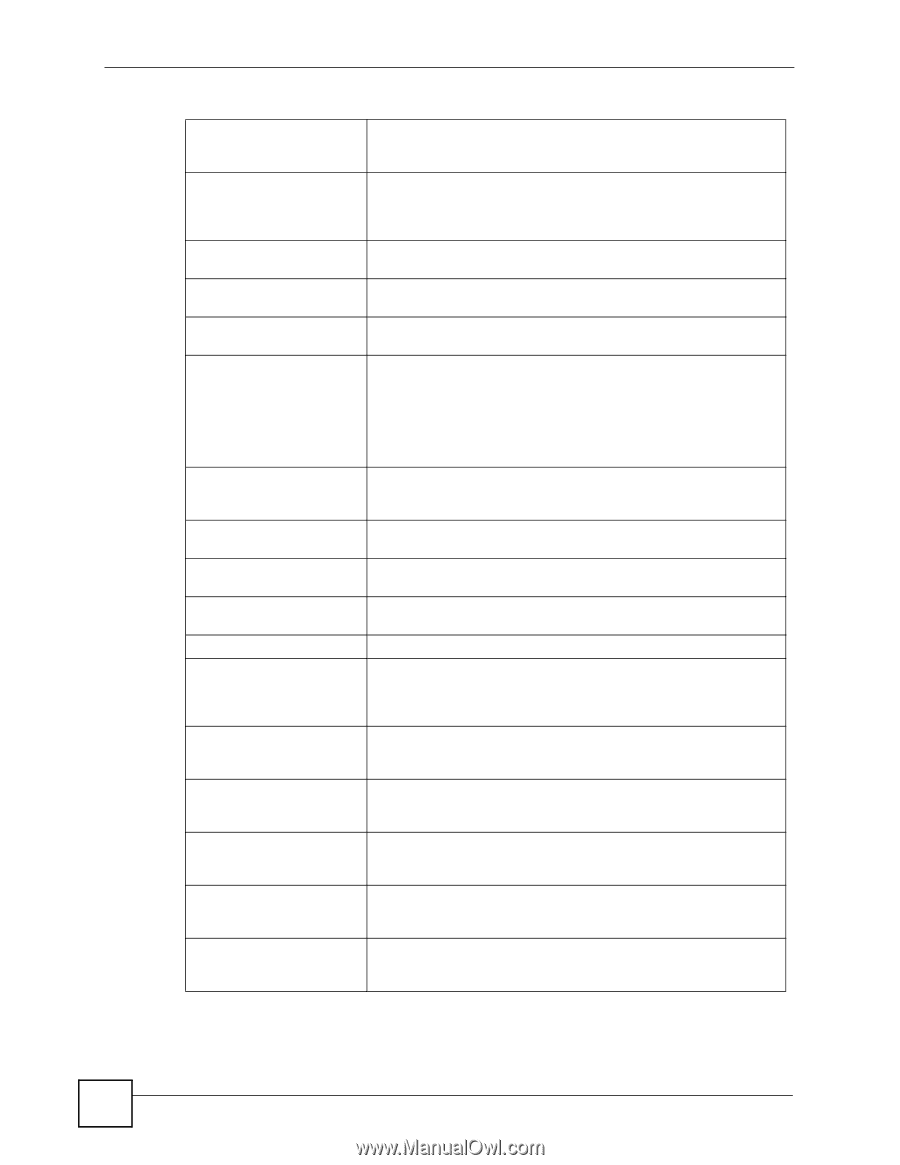
Chapter 13 Product Specifications Table 110 Firmware Features (continued) Disk Quota Use the disk quota feature to stop one user(s) from using up all disk capacity by setting a limit on how much storage space he/she may use. User Passwords Configure a password for an individual User to restrict access to the NSA. Non-admin users can change their own passwords by accessing the Web Configurator. The Change Password screen appears when a username other than "admin" is entered. Volume Encryption The NSA can create encrypted volumes so an attacker who removes the physical drive still cannot read the data. ACL The Access Control List (ACL) defines user read/write permissions for specific files and/or folders. Storage Event Logs The NSA can keep detailed records of all user access to files and folders. Workgroup and Domain Security Modes For Windows or Mac OSX users (using the Common Internet File System (CIFS) protocol for remote file access) you can configure Workgroup mode requiring users to log in with a user name and password. These user and group accounts are maintained on the NSA. For a large number of CIFS users where accounts are stored on an external server, you can use Domain security mode (Primary Domain Controller) Client Support Data can be shared among all Windows, Mac, Linux, and UNIX users that have FTP client software or CIFS file sharing support (such as Samba for Linux and UNIX users). IEEE 802.3d Ethernet Failover LAN2 can backup LAN1. If LAN1 loses its connection, LAN2 takes over LAN1's IP address and traffic. IEEE 802.3d Ethernet Load The NSA can distribute the traffic load across LAN1 and LAN2. Balance HTTP/HTTPS Access the NSA using a regular web connection (HTTP) or an encrypted web connection (HTTPS) using secure socket layer (SSL). SSL Certificate Manager The NSA can generate certificates and certificate requests. DHCP (Dynamic Host Configuration Protocol) DHCP (Dynamic Host Configuration Protocol) allows the NSA to obtain an IP address and subnet mask at start-up from a centralized DHCP server. Alternatively, you can give the NSA a static IP address and subnet mask. Full Network Management The embedded Web Configurator is an platform-independent webbased utility that allows you to easily access the NSA's management settings. Firmware Upload and Configuration File Management Upload new firmware to the NSA using the Web Configurator. You can also back up and restore the NSA configuration file containing all its settings to/from your computer. NSA Discovery Utility (NDU) Use the NDU from a Windows computer to find NSA(s) in your network, access the NSA login page, change its IP address configuration or map to a Windows network drive. Genie Backup Manager Genie Backup Manager is a tool for Windows users to create (and schedule) backups of data stored on their Windows computer to an NSA. S.M.A.R.T. The NSA can use the S.M.A.R.T. (Self-Monitoring, Analysis, and Reporting Technology) monitoring system to detect and report on hard drive reliability indicators to help anticipate hard drive failures. 258 NSA-2401 User's Guide