ZyXEL NWA1123-NI User Guide - Page 59
Passphrase, Encryption, RADIUS
 |
View all ZyXEL NWA1123-NI manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 59 highlights
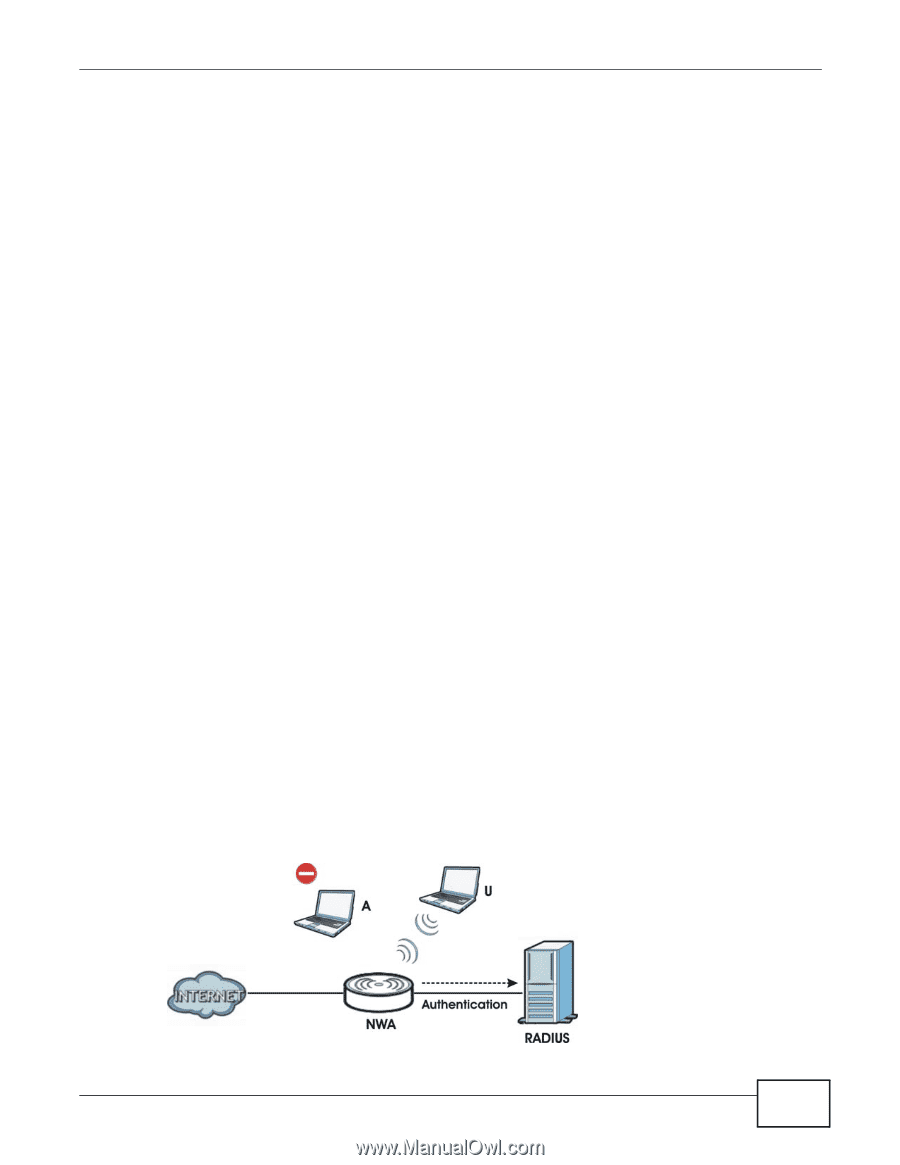
Chapter 6 Wireless LAN Passphrase A passphrase functions like a password. In WEP security mode, it is further converted by the NWA into a complicated string that is referred to as the "key". This key is requested from all devices wishing to connect to a wireless network. PSK The Pre-Shared Key (PSK) is a password shared by a wireless access point and a client during a previous secure connection. The key can then be used to establish a connection between the two parties. Encryption Wireless networks can use encryption to protect the information that is sent in the wireless network. Encryption is like a secret code. If you do not know the secret code, you cannot understand the message. Encryption is the process of converting data into unreadable text. This secures information in network communications. The intended recipient of the data can "unlock" it with a pre-assigned key, making the information readable only to him. The NWA when used as a wireless client employs Temporal Key Integrity Protocol (TKIP) data encryption. EAP Extensible Authentication Protocol (EAP) is a protocol used by a wireless client, an access point and an authentication server to negotiate a connection. The EAP methods employed by the NWA when in Wireless Client operating mode are Transport Layer Security (TLS), Protected Extensible Authentication Protocol (PEAP), Lightweight Extensible Authentication Protocol (LEAP) and Tunneled Transport Layer Security (TTLS). The authentication protocol may either be Microsoft Challenge Handshake Authentication Protocol Version 2 (MSCHAPv2) or Generic Token Card (GTC). Further information on these terms can be found in Appendix E on page 187. RADIUS Remote Authentication Dial In User Service (RADIUS) is a protocol that can be used to manage user access to large networks. It is based on a client-server model that supports authentication, authorization and accounting. The access point is the client and the server is the RADIUS server. Figure 21 RADIUS Server Setup NWA1120 Series User's Guide 59