Cisco WS-CE500-24TT Administration Guide - Page 31
Scenario 8: Configuring ProtectLink Web & Email Security
 |
UPC - 882658054068
View all Cisco WS-CE500-24TT manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 31 highlights
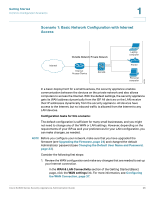
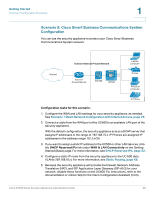
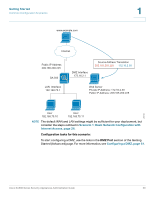
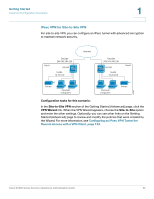
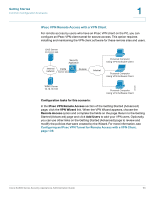
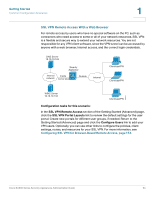
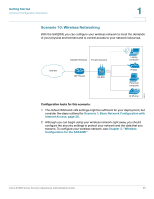
Getting Started Common Configuration Scenarios 1 Scenario 8: Configuring ProtectLink Web & Email Security For added protection against web and email threats, the security appliance supports Cisco ProtectLink Security services. By using these services, your network is protected from email threats in the Internet "cloud" and web threats in the Cisco security appliance, providing access only to email and websites that are appropriate for your business. Configuration tasks for this scenario: In the ProtectLink Web & Email Security section of the Getting Started (Advanced) page, click Enable ProtectLink Gateway and/or Endpoint. The Protect Link window opens. For more information, see Chapter 6, "Using Cisco ProtectLink Security Services." Scenario 9: Site-to-Site Networking and Remote Access You can configure a Virtual Private Network (VPN) to extend your network to other sites or to allow business partners and teleworkers to access applications and network resources. You can configure the following types of VPNs: • IPsec VPN for a Site-to-Site Tunnel • IPsec VPN for Remote Access with a VPN Client • SSL VPN for Remote Access with a Web Browser Cisco SA500 Series Security Appliances Administration Guide 31