McAfee NAPCKE-AB-AA Configuration Guide - Page 47
Reports tab
 |
View all McAfee NAPCKE-AB-AA manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 47 highlights
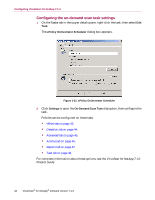
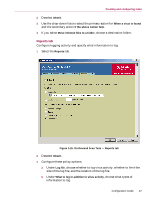
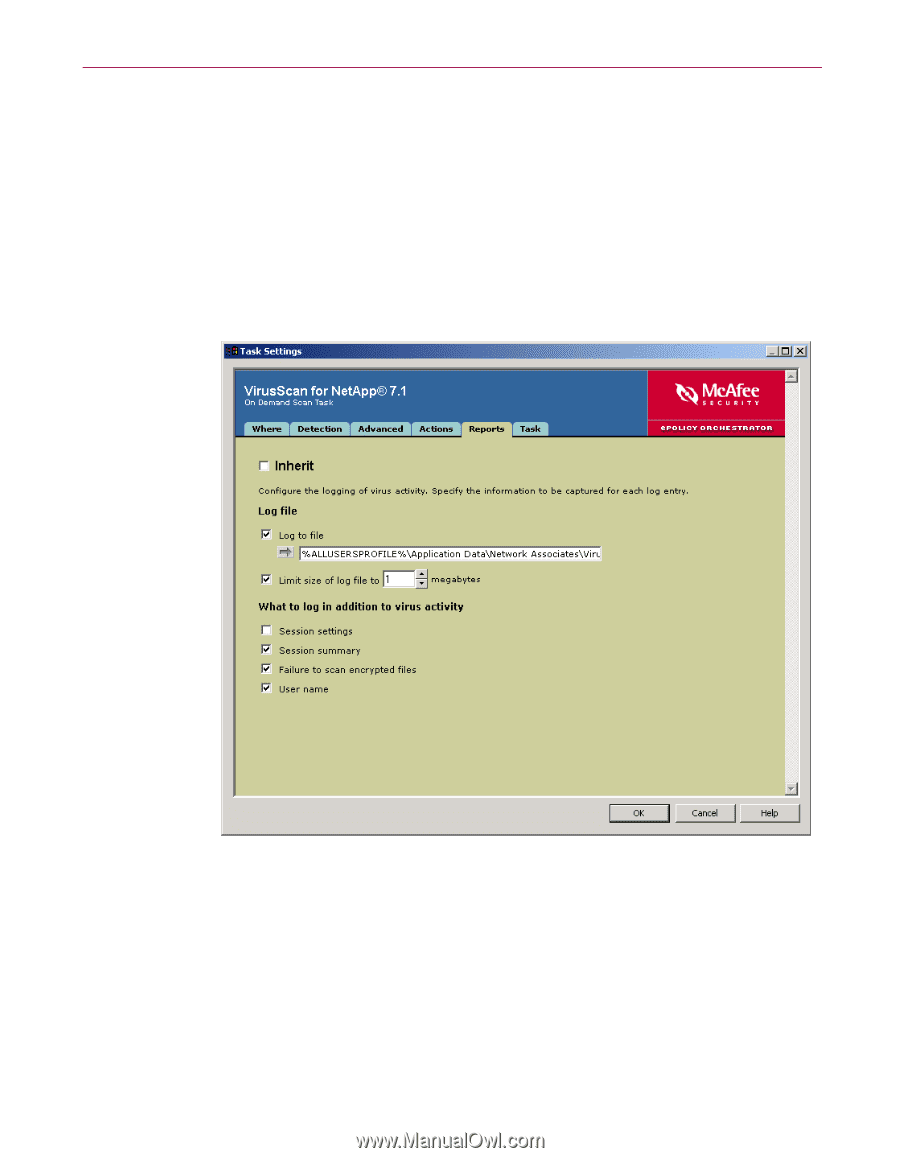
Creating and configuring tasks 2 Deselect Inherit. 3 Use the drop-down lists to select the primary action for When a virus is found and the secondary action If the above Action fails. 4 If you select Move infected files to a folder, choose a destination folder. Reports tab Configure logging activity and specify what information to log. 1 Select the Reports tab. Figure 1-26. On-Demand Scan Task - Reports tab 2 Deselect Inherit. 3 Configure these policy options: a Under Log file, choose whether to log virus activity, whether to limit the size of the log file, and the location of the log file. b Under What to log in addition to virus activity, choose what types of information to log. Configuration Guide 47
Configuration Guide
47
Creating and configuring tasks
2
Deselect
Inherit
.
3
Use the drop-down lists to select the primary action for
When a virus is found
and the secondary action
If the above Action fails
.
4
If you select
Move infected files to a folder
, choose a destination folder.
Reports tab
Configure logging activity and specify what information to log.
1
Select the
Reports
tab.
2
Deselect
Inherit
.
3
Configure these policy options:
a
Under
Log file
, choose whether to log virus activity, whether to limit the
size of the log file, and the location of the log file.
b
Under
What to log in addition to virus activity
, choose what types of
information to log.
Figure 1-26. On-Demand Scan Task — Reports tab