Ricoh Aficio SP C821DNT1 Design Guide - Page 14
Data Security, 3-1 External I/F, 3-2 Protection of Program Data from Illegal Access via an External
 |
View all Ricoh Aficio SP C821DNT1 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 14 highlights
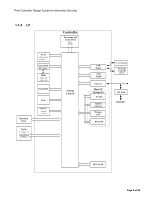
Print Controller Design Guide for Information Security 1-3 Data Security 1-3-1 External I/F The MFP/LP is equipped with the following external interfaces: • Serial I/F for connection of external coin/card-operated devices. • Serial I/F for connection of peripheral devices (e.g. DF, Finisher, LCT). • Analog G3 FAX I/F (public telecommunications line), G4 FAX I/F (ISDN). • Standard IEEE 1284 parallel I/F (Host I/F), which can function as a two-way parallel interface when using a USB cable. • Standard IEEE 1394 I/F • 100BASE-TX and 10BASE-T compatible network I/F (Host I/F) • Gigabit Ethernet-compatible network I/F (Host I/F options, external controller I/F board) • Standard IEEE802.11b wireless LAN network I/F (Host I/F option) • Bluetooth I/F (Host I/F option) • USB2.0 Type B I/F (Host I/F) • USB2.0 Type A I/F (IC card, Pictbridge) 1-3-2 Protection of Program Data from Illegal Access via an External Device 1. All of the above principal machine functions, as well as software for all shared service layers, run on the UNIX operating system as independent processes (data/program modules). Memory space is allocated specifically for each module, which makes it impossible for one module to directly access the memory space of any other. 2. Data transfer between modules is Unix socket-based, whereby communication is performed along ID-protected communication paths. This ensures exclusive connections among the modules present in the MFP/LP, thereby preventing access by any module outside this pre-determined set. For example, incoming FAX data will only be sent to those modules designated to perform FAX data operations. This arrangement prevents illegal access to networks and internal programs from an outside line. 3. All image data stored on the HDD or stored temporarily in the Image Memory is managed by a memory control module called the MCS (Memory Control Service), which ensures that the data can only be accessed by specified machine function(s). In addition, this arrangement prevents illegal access to this data from an outside line. User data, such as the Address Book data stored in the HDD/flash ROM and User Code data stored in the NV-RAM, is managed by the UCS module. Access to this data is not possible by any module except those pre-determined modules in the MFP/LP itself. This arrangement ensures that the data stored in the MFP/LP cannot be accessed illegally via an external I/F. Page 14 of 86