Ricoh Aficio SP C821DNT1 Design Guide - Page 71
Server Documents MFP models only
 |
View all Ricoh Aficio SP C821DNT1 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 71 highlights
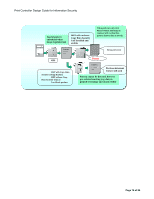
Print Controller Design Guide for Information Security Data Flow WebDocBox supports HTTP, a protocol used by Web browsers installed on network-connected computers. The session is initiated when the first request for connection is received from the Web browser, after which WebDocBox sends commands to the shared service layers in accordance with the specific operations requested. If 30 minutes passes with no additional access attempts from the same browser, the session is terminated. To initiate a new session, it is then necessary to access the WebDocBox top page (the main screen that displays the list of Document Server files). Data Security Considerations As a security feature common to all Web applications, it is possible to perform access control by allowing connection only with users who provide a specific IP address when the session is initiated. Users who do not provide an authorized IP address are not even able to view Document Server data. In addition, it is possible to prevent the viewing and altering of data through the use of encrypted communication (HTTPS over SSL). With the use of User Authentication, it is possible to limit the conditions under which remote operations can be performed on Document Server files. Only users who have been pre-approved for access and clear the authentication process are allowed to perform the remote operations. Additionally, it is possible to place limits on the specific operations that each registered user is capable of performing. Users are unable to perform operations that have been prohibited, even if they clear the authentication process. This prevents any potential leakage or alteration of image data. It is possible to protect individual Document Server documents with a password (see 1.7.2 Document Server Documents (MFP models only) for more details). It is possible to restrict remote access to stored documents using the same ACL mentioned in section 1.52. Users logged in as Document Administrators are able to disable the password lock as well as view, edit and delete all documents. However, Document Administrators are not able to send (FAX, e-mail, forward), capture or print out the documents. When sending stored image files to the PC in PDF format, it is possible to encrypt the file as well as set a password for decrypting the PDF data at the PC side. This prevents any illegal use of the data in the unlikely event the transmission is intercepted. When transmitting stored Scanner files as e-mail attachments, using S/MIME, it is possible to encrypt the entire e-mail (incl. the file attachment), as well as attach a digital signature. This precludes the possibility of data leakage, data alteration, and sender impersonation. Page 71 of 86