Cisco SPA2102-AU Provisioning Guide - Page 24
Numeric Code, Cipher Suite, TLS_DHE_RSA_WITH_AES_256_CBC_SHA - firmware update
 |
View all Cisco SPA2102-AU manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 24 highlights
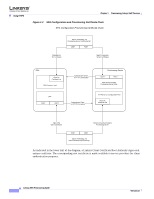
Provisioning Setup Chapter 1 Provisioning Linksys VoIP Devices To determine if a SPA carries an individualized certificate use the $CCERT provisioning macro variable, whose value expands to either Installed or Not Installed, according to the presence or absence of a unique client certificate. In the case of a generic certificate, it is possible to obtain the serial number of the unit from the HTTP request header, in the User-Agent field. HTTPS servers can be configured to request SSL certificates from connecting clients. If enabled, the server can verify the client certificate chain using the Linksys CA Client Root Certificate supplied by Linksys. It can then provide the certificate information to a CGI for further processing. The location for storing certificates may vary. For example, on a Apache installation, the file paths for storing the provisioning server signed certificate, its associated private key, and the Linksys CA client root certificate are likely to be as follows: # Server Certificate: SSLCertificateFile /etc/httpd/conf/provserver.crt # Server Private Key: SSLCertificateKeyFile /etc/httpd/conf/provserver.key # Certificate Authority (CA): SSLCACertificateFile /etc/httpd/conf/spacroot.crt Refer to the documentation provided for an HTTPS server for specific information. Firmware release 2.0.6 supports the following cipher suites for SSL connection to a server using HTTPS. Future release updates may implement additional cipher suites. Table 1-2 Cipher Suites Supported for Connecting to an HTTPS Server Numeric Code 0x0039 0x0035 0x0033 0x002f 0x0005 0x0004 0x0062 0x0060 0x0003 Cipher Suite TLS_DHE_RSA_WITH_AES_256_CBC_SHA TLS_RSA_WITH_AES_256_CBC_SHA TLS_DHE_RSA_WITH_AES_128_CBC_SHA TLS_RSA_WITH_AES_128_CBC_SHA TLS_RSA_WITH_RC4_128_SHA TLS_RSA_WITH_RC4_128_MD5 TLS_RSA_EXPORT1024_WITH_RC4_56_SHA TLS_RSA_EXPORT1024_WITH_RC4_56_MD5 TLS_RSA_EXPORT_WITH_RC4_40_MD5 1-14 Linksys SPA Provisioning Guide Version 3.0