D-Link DS-510S User Guide - Page 64
Firewall
 |
View all D-Link DS-510S manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 64 highlights
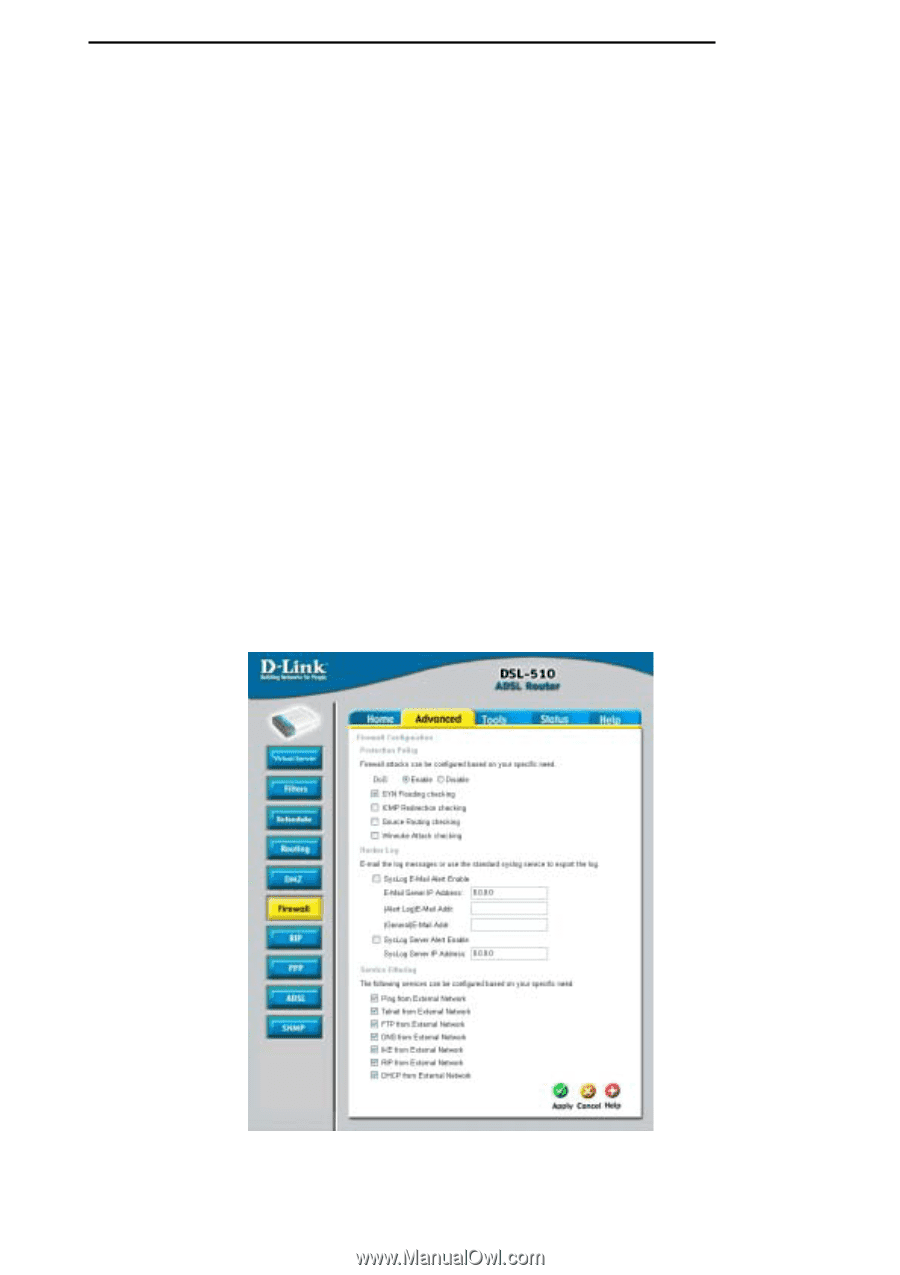
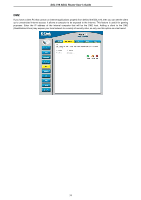
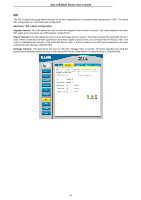
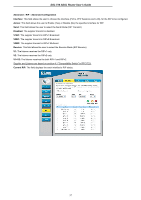
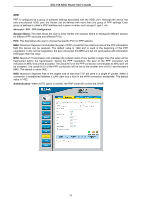
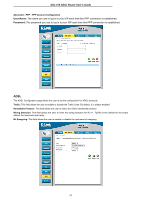
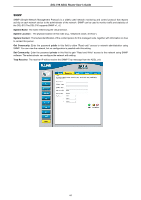
DSL-510 ADSL Router User's Guide Firewall Firewall Rules is an advance feature used to deny or allow traffic from passing through the DSL-510. It works in the same way as IP Filters with additional settings. You can create more detailed rules for the Router. DoS Protection: Click the Enable radio button to use the following denial of service protection: (1)SYN DoS (2)ICMP DoS (3)Per-host DoS protection SYN Flooding checking: is a well-known Denial Of Service attack on TCP based services. TCP needs a 3-way handshake before the actual communication starts between two hosts. Whenever a new connection request comes in, the server allocates some resources for serving it. A malicious intruder can forge a huge amount of service requests over a very short period, and make your server run out of its resources. When you enable SYN flooding control, filters out such forged service requests while allowing legitimate requests to pass through. ICMP Redirection checking: is a standard ICMP message, which conveys the better route information to the source. After receiving this message, the recipient updates its routing table with the routing information present in the message. As there is no strong authentication mechanism built into this process, an intruder can make a target update its routing table with the information of his/her interest. By this way an intruder can potentially get access to the data originated from the target host. Source Routing checking: With strict and loose source routing, as specified in IP standard RFC 791, one can make data grams take a predefined path towards a destination. By this way, an intruder can gain more information about the corporate network, which he or she can then misuse. Winnuke Attack checking: Apparently Windows doesn't know how to handle OOB, so it panics and crazy things happen. Windows also sometimes has trouble handling anything on a network at all after an attack like this. A reboot fixes whatever damage this causes. Hacker Log SysLog: Specifies how attempted violations of the firewall settings will be tracked. Records of such events can be sent via Ethernet to be handled by a system utility Ethernet to (trace) or can e-mailed to specified administrators. E-mail Address: Specifies the e-mail addresses of the administrators who should receive notices of any attempted firewall violations. Service Filtering: With this table you can define the transport protocol and used port for the services. 55