HP AE370A HP StorageWorks Fabric OS 6.x administrator guide (5697-7344, March - Page 128
Zeroization functions, Table 40 Zeroization behavior, Power-up self tests
 |
UPC - 882780362611
View all HP AE370A manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 128 highlights
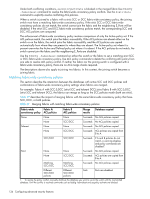
Zeroization functions Explicit zeroization can be done at the discretion of the security administrator. These functions clear the passwords and the shared secrets. The following table lists the various keys used in the system that will be zeroized in a FIPS compliant FOS module. Table 40 Zeroization behavior Keys DH Private keys Zeroization CLI No CLI required FCSP Challenge Handshake Authentication Protocol (CHAP) Secret secauthsecret --remove FCAP Private Key pkiremove SSH Session Key No CLI required SSH RSA private Key No CLI required RNG Seed Key No CLI required Passwords passwddefault fipscfg --zeroize TLS private keys seccertutil delkey TLS pre-master secret TLS session key TLS authentication key RADIUS secret No CLI required No CLI required No CLI required aaaconfig --remove Description Keys will be zeroized within code before they are released from memory. The secauthsecret -remove is used to remove/zeroize the keys. The pkicreate command creates the keys, and 'pkiremove' removes/zeroizes the keys. This is generated for each SSH session that is established to and from the host. It automatically zeroizes on session termination. Key based SSH authentication is not used for SSH sessions. /dev/urandom is used as the initial source of seed for RNG. RNG seed key is zeroized on every random number generation. This will remove user defined accounts in addition to default passwords for the root, admin, and user default accounts. However only root has permissions for this command. So securityadmin and admin roles need to use fipscfg --zeroize which in addition to removing user accounts and resetting passwords, also does the complete zerioization of the system. The command seccertutil delkey is used to zeroize these keys. Automatically zeroized on session termination Automatically zeroized on session termination Automatically zeroized on session termination The aaaconfig --remove zeroizes the secret and deletes a configured server Power-up self tests The self tests are invoked by powering on the switch in FIPS mode and do not require any operator intervention. These tests can also be invoked by the user through a CLI interface. NOTE: Perform power-on self-tests. If any of KAT tests fail, the switch goes into a FIPS Error state which is to reboot the system to single-user mode. You will need to perform a recovery procedure by booting into single-user mode to recover the system. 128 Configuring advanced security features