Ricoh Aficio SP C820DNT1 Design Guide - Page 20
Verification of Firmware/Program Validity
 |
View all Ricoh Aficio SP C820DNT1 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 20 highlights
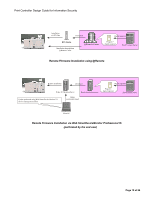
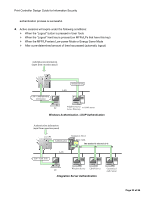
Print Controller Design Guide for Information Security 1-4-2 Verification of Firmware/Program Validity Overview In order to continually ensure the validity of all controller core programs and application firmware installed on the MFP/LP at the time of product shipment, as well as those that are newly installed as updates through the process explained in section 1.4.1 above, the MFP/LP performs a validation process known as Trusted Boot every time the main system is booted up. Covering the range of software from boot programs to end-point functions and applications, the Trusted Boot validation process provides comprehensive, TPM-based security. The MFP/LP uses the unique digital signature assigned to each program/firmware in order to judge its validity. The public key used for this verification is stored in an overwrite-protected, non-volatile region of the TPM, which makes it extremely difficult for the key itself to be altered in any way, providing additional protection of the programs/firmware. Trusted Boot employs two methods to verify the validity of the programs/firmware mentioned above: RTM (Root Trust of Measurement) is used to validate the controller core programs, which include the MFP/LP operating system, BIOS, and boot loader. Using the TPM, this method is capable of detecting any alterations made to these programs. The same digital signature-based verification process explained in section 1.4.1 is used to validate the application firmware Trusted Boot is integrated with the protection of the user's encryption keys (see section 1.8 for details), ensuring that only valid programs are given access to these keys. Note: Produced by STMicroelectronics, TPM is a product of the ST19WP18 family, which has earned Common Criteria certification (EAL5+). Page 20 of 86