Ricoh Aficio SP C820DNT1 Design Guide - Page 74
The Copy Data Security Feature, 2-1 Overview of Copy Data Security Operations
 |
View all Ricoh Aficio SP C820DNT1 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 74 highlights
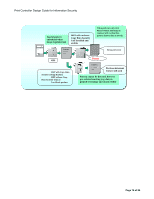
Print Controller Design Guide for Information Security 3-2 The "Copy Data Security" Feature 3-2-1 Overview of Copy Data Security Operations The Copy Data Security feature acts to discourage unauthorized copying of confidential documents. There are two aspects to the feature: Marking the copy/print with a visible, embedded pattern Note: The marking aspect is a standard feature on MFP/LP models. Detecting the pattern if a copy is attempted, and then replacing the image with a vertical line pattern Note: The detection aspect is provided as an optional feature on MFP models only (Copy Data Security Unit). Marking: If the user selects the Copy Data Security feature when making the first copy of a document or printing out the document for the first time from the printer driver, a pre-defined pattern will be embedded in the background area of the resulting image to demarcate that copying of the image is prohibited. Users can select from among several patterns, as well as add a text string such as "Copying of this document is prohibited" or the date, time or name of the user who created the original document (details below). Note: Documents for which the Copy Data Security feature has been selected cannot be saved to the Document Server. Detection, replacing image with vertical line pattern: If a user then attempts to make a copy of an image containing the embedded pattern (or store the image to the MFP Document Server), and the optional Copy Data Security Unit is installed on that MFP, the pattern will be detected and a buzzer will sound. Then, on the printout, the original image is replaced with a vertical line pattern. The amount of toner consumed by this vertical line pattern can be adjusted separately for each of the relevant MFP functions: Copier, Scanner, and FAX. There are four vertical line patterns from which to choose, ranging from high to low toner consumption (the more toner consumed, the narrower the interval between the lines in the pattern). The default setting, which consumes the most toner, is roughly equivalent to a solid gray image. In addition, a log entry of the event will be added to the access log, along with the date, time and username. If a user attempts to make a copy of an image containing the embedded pattern on an MFP (incl. non-Ricoh products) on which the optional Copy Data Security Unit is not installed, the resulting image will not be replaced with the vertical line pattern, but will be much more indecipherable due to the superimposition of the selected pattern on the original image. In addition, if the user entered a text string to be embedded into the pattern when printing out the original document, the text will be made Page 74 of 86